Layer 2 -- My study notes and study technique, starting with My background experiences and expactations
Page 1 of 1
 Layer 2 -- My study notes and study technique, starting with My background experiences and expactations
Layer 2 -- My study notes and study technique, starting with My background experiences and expactations
Some personal information:
My name is Daniel Larsson, and I am currently working as a Consultant. More specifically IT-Consultant with Network Engineering as a speciality. For as long as I can remember I have Always been interested in computer networks and Communication, it's been my passion for many years. I've been working on and off within the IT-Field for about 12 years. Always as a technician or an Engineer. I've not Always worked with networking, but I've Always been interested in it so even if it's not been my main profession for half my technician time it's Always been my off-work hours passion.
For a long time i made the decision to not work with my hobby and passion becuase i was afraid i would get bored of it, but that turned out to be wrong. Now I'm more than ever happily working with networking and engineering since a few years back. And I don't regret it at all.
Basically my background experiences puts me in about 13 years working as a technician and engineer. About 7 of those years within networking and the rest within Electrical Engineering or IT Support of some sort. In short I have seen my fair share of poorly designed and performed networks. But Before I had to start working I also was very interested in networking and we can say that my hobby started when i was about 6 and have not ended yet. I started with networking back in 1989 with a 9600BPS modem Connection. Experiencing the pain with IPX and the early PAIN with TCP/IP as well.
So i will say that i have a fairly good background experience.
How long have I been studying for CCIE?
Basically the last 6-7 years. Not specifically studying for just the CCIE but it's been my long term goal for the last 6-7 years. So i guess I could say that my journey started in about 2007-2008. And when i say that i've not been specifically studying for CCIE R&S i mean that I have been studying a lot of networking, but not specifically the CCIE R&S. For example i've been studying the following:
-CCNA R&S
-CCNP R&S
-CCDA
-CCDP
-CCNA Wireless
-CCNA Security
-CCNP Security
-CCNA Voice
-CCNA Datacenter
All ultimately making me a better engineer, and I have also learned that it helped me a lot with my CCIE Studies becuase i have a very good and solid background experience with theory from all tracks.
When do you plan on taking the CCIE RSv5 Exam?
When I'm ready. Or i should say, when i Do feel ready. I could easily pass the Written exam, I consider myself a CCIE engineer when it comes to network understanding. My current plans are that sometime within the next year i will make an attempt on the lab to see where I stand. If i fail utterly, i will postpone it. If i feel like I'm doing good then i will go for it in 2016.
My name is Daniel Larsson, and I am currently working as a Consultant. More specifically IT-Consultant with Network Engineering as a speciality. For as long as I can remember I have Always been interested in computer networks and Communication, it's been my passion for many years. I've been working on and off within the IT-Field for about 12 years. Always as a technician or an Engineer. I've not Always worked with networking, but I've Always been interested in it so even if it's not been my main profession for half my technician time it's Always been my off-work hours passion.
For a long time i made the decision to not work with my hobby and passion becuase i was afraid i would get bored of it, but that turned out to be wrong. Now I'm more than ever happily working with networking and engineering since a few years back. And I don't regret it at all.
Basically my background experiences puts me in about 13 years working as a technician and engineer. About 7 of those years within networking and the rest within Electrical Engineering or IT Support of some sort. In short I have seen my fair share of poorly designed and performed networks. But Before I had to start working I also was very interested in networking and we can say that my hobby started when i was about 6 and have not ended yet. I started with networking back in 1989 with a 9600BPS modem Connection. Experiencing the pain with IPX and the early PAIN with TCP/IP as well.
So i will say that i have a fairly good background experience.
How long have I been studying for CCIE?
Basically the last 6-7 years. Not specifically studying for just the CCIE but it's been my long term goal for the last 6-7 years. So i guess I could say that my journey started in about 2007-2008. And when i say that i've not been specifically studying for CCIE R&S i mean that I have been studying a lot of networking, but not specifically the CCIE R&S. For example i've been studying the following:
-CCNA R&S
-CCNP R&S
-CCDA
-CCDP
-CCNA Wireless
-CCNA Security
-CCNP Security
-CCNA Voice
-CCNA Datacenter
All ultimately making me a better engineer, and I have also learned that it helped me a lot with my CCIE Studies becuase i have a very good and solid background experience with theory from all tracks.
When do you plan on taking the CCIE RSv5 Exam?
When I'm ready. Or i should say, when i Do feel ready. I could easily pass the Written exam, I consider myself a CCIE engineer when it comes to network understanding. My current plans are that sometime within the next year i will make an attempt on the lab to see where I stand. If i fail utterly, i will postpone it. If i feel like I'm doing good then i will go for it in 2016.
Last edited by daniel.larsson on Fri May 15, 2015 12:26 pm; edited 7 times in total
 My way of studying in depth
My way of studying in depth
There are plenty of ways to study for an exam, and plenty of ways to prepare for an exam. This is just one of the techniques you can use, and this is the technique that is working very well for me. Since this is a studygroup i will not explain the details, i will just share the way im studying and also my study notes along the way through each CCIE RSv5 topic. I Think we all can agree that there is going to be some kind of dedication needed to pass this exam. And for me that dedication is Writing down everytime i study what i learn and which topics i studied.
All-in-all though I would say that i'm roughly 50% through with my studies Before I will book the exam. So it's still a long journey! But I recently got asked how to prepare for the exam at Another Place so i will just add it in here as well for the information. So i quote:
While studying for the CCIE i tend to write a lot in my study-document to help with the learning process and to keep me motivated. But basically this is how I study and I quote my "little" document:
General study technique that eventually will make me a master of the CCIE RSv5 topics. Consisting of three basic steps.
Do this for each and every topic that is in the CCIE RSv5 LAB blueprint. Layer 2 technologies consists of roughly 10-15% of the CCIE RSv5 LAB so it's doable in reasonable amount of time. As a preparation for CCIE i have also noted my preparation time in this document listed by a per-technology basis. It will keep me reminded about how much time is invested in each topic in case i need to go back and study some more.
I will approach this lab by learning from scratch, meaning that I will read all design documents and all release notes about all the technologies that are listed in the CCIE RSv5 blueprint just to be sure I at least have a decent chance of remembering reading about it in case i get tested on it during the lab.
For instance, i feel extremely confident in basic and advanced L2 technologies (STP, VLANs, Trunks, Etherchannels, VTP and so on) but I will still read through every "core" document by cisco on the technologies I can be tested on.
As a final note i would just like to say that this technique may not work for all. In fact it may only work for me, but it works really well for me! I personally strongly recommend a simular approach of studying. Mainly because in this way you will learn what you DON'T already know and that will be your weakest area. So it will Always be good to get that on paper so you know what you need to study instead of studying what you already know!
The complete way of studying that I am preparing for the CCIE RSv5 Blueprint is how Brian McGahan reordered it. It makes perfect sense. Most of the topics i'll post below are my study notes and you'll see that they follow this list very much. I've made some Changes mainly in the Security part because I prefer to be through-and-done with a topic rather than go back at a later stage. I then cross every topic out of the list as I've studied them. That doesn't mean that I am ready with them, just that I have at least a foundational knowledge about them. It also helps with knowing how long away the Lab date is!
This is the list:
RSv5 Expanded Blueprint
Color explanation
Red = Not studied topics. (meaning I have not studies these topics at CCIE Level)
Blue = Studied topics that I consider myself Confident enough in.
Dark Red = Studied topics but I feel that I need to improve on Before lab.
Black = Topics initially in the Blueprint but was later removed.
Striked = Topic from the CCIE RSv5 Blueprint that has been covered in studies.
1. LAN Switching
..1.1. VLANs & Trunking
....1.1.1. Standard VLANs
....1.1.2. Extended VLANs
....1.1.3. VLAN Database
....1.1.4. Access Ports
....1.1.5. 802.1q Trunk Ports
....1.1.6. 802.1q Native VLAN
....1.1.7. Dynamic Trunking Protocol (DTP)
....1.1.8. Trunking Allowed List
..1.2. VTP
....1.2.1. VTP Version 1, 2, & 3
....1.2.2. VTP Authentication
....1.2.3. VTP Pruning
....1.2.4. VTP Prune Eligible List
....1.2.5. VTPv3 & Private VLANs
..1.3. EtherChannels
....1.3.1. Static Layer 2 EtherChannels
....1.3.2. PAgP
....1.3.3. LACP
....1.3.4. Layer 3 EtherChannel
....1.3.5. EtherChannel Load Balancing
....1.3.6. EtherChannel Protocol Limiting
....1.3.7. EtherChannel Misconfig Guard
..1.4. Spanning-Tree Protocol
....1.4.1. PVST+
......1.4.1.1. STP Root Bridge Election
......1.4.1.2. STP Path Selection with Port Cost
......1.4.1.3. STP Path Selection with Port Priority
......1.4.1.4. STP Convergence Timers
....1.4.2. Optional STP Features 1.4.2.1. PortFast
......1.4.2.2. UplinkFast
......1.4.2.3. BackboneFast
......1.4.2.4. BPDU Guard
......1.4.2.5. BPDU Filter
......1.4.2.6. Root Guard
....1.4.3. Rapid-PVST+
......1.4.3.1. RSTP Convergence Optimizations
......1.4.3.2. Edge Ports
....1.4.4. Multiple STP
......1.4.4.1. MST Root Bridge Election
......1.4.4.2. MST Path Selection with Port Cost
......1.4.4.3. MST Path Selection with Port Priority
......1.4.4.4. MST and CST/PVST+ Interoperability
......1.4.4.5. Multi-Region MST
..1.5. 802.1q Tunneling
....1.5.1. L2 Protocol Tunneling
....1.5.2. Layer 2 MTU
....1.5.3. EtherChannel over 802.1q Tunneling
..1.6. Miscellaneous
....1.6.1. CDP
....1.6.2. LLDP
....1.6.3. UDLD
....1.6.4. CAM Aging Time
....1.6.5. SPAN
....1.6.6. RSPAN
....1.6.7. ERSPAN
....1.6.8. Flex Links
....1.6.9. Fallback Bridging
....1.6.10. Voice VLANs
....1.6.11. Smartport Macros
2. Layer 2 WAN Circuits
..2.1. HDLC
..2.2. PPP
..2.3. PPP Authentication
..2.4. PPP Multilink
..2.5. PPPoE
All-in-all though I would say that i'm roughly 50% through with my studies Before I will book the exam. So it's still a long journey! But I recently got asked how to prepare for the exam at Another Place so i will just add it in here as well for the information. So i quote:
Daniel Larsson wrote:I do get asked a lot of questions of how to prepare for exams or how to best learn a specific topic. I am slowly (too slowly) preparing myself for the RSv5 Lab exam and someone might find it interesting to know how to prepare for an exam like that.
So someone might find this interesting, but this is actually how I am currently studying for both CCDP and the CCIE RSv5 Lab. I find this technique to work very well for me and it makes sure I don't oversee any small details or any topic that I haven't heard of before.
This is a copy-and-paste from my CCIE Study-nots document, so mind the words used ;-).
While studying for the CCIE i tend to write a lot in my study-document to help with the learning process and to keep me motivated. But basically this is how I study and I quote my "little" document:
General study technique that eventually will make me a master of the CCIE RSv5 topics. Consisting of three basic steps.
- -First, read through the configuration and technology explanations on the 3750-X switching platforms.
- -Secondly, watch INE CCIE videos about the topics to learn more in depth.
- -And lastly, lab it up using INE CCIE RSv5 topology and using their CCIE Workbook
Do this for each and every topic that is in the CCIE RSv5 LAB blueprint. Layer 2 technologies consists of roughly 10-15% of the CCIE RSv5 LAB so it's doable in reasonable amount of time. As a preparation for CCIE i have also noted my preparation time in this document listed by a per-technology basis. It will keep me reminded about how much time is invested in each topic in case i need to go back and study some more.
I will approach this lab by learning from scratch, meaning that I will read all design documents and all release notes about all the technologies that are listed in the CCIE RSv5 blueprint just to be sure I at least have a decent chance of remembering reading about it in case i get tested on it during the lab.
For instance, i feel extremely confident in basic and advanced L2 technologies (STP, VLANs, Trunks, Etherchannels, VTP and so on) but I will still read through every "core" document by cisco on the technologies I can be tested on.
As a final note i would just like to say that this technique may not work for all. In fact it may only work for me, but it works really well for me! I personally strongly recommend a simular approach of studying. Mainly because in this way you will learn what you DON'T already know and that will be your weakest area. So it will Always be good to get that on paper so you know what you need to study instead of studying what you already know!
The complete way of studying that I am preparing for the CCIE RSv5 Blueprint is how Brian McGahan reordered it. It makes perfect sense. Most of the topics i'll post below are my study notes and you'll see that they follow this list very much. I've made some Changes mainly in the Security part because I prefer to be through-and-done with a topic rather than go back at a later stage. I then cross every topic out of the list as I've studied them. That doesn't mean that I am ready with them, just that I have at least a foundational knowledge about them. It also helps with knowing how long away the Lab date is!
This is the list:
RSv5 Expanded Blueprint
Color explanation
Red = Not studied topics. (meaning I have not studies these topics at CCIE Level)
Blue = Studied topics that I consider myself Confident enough in.
Dark Red = Studied topics but I feel that I need to improve on Before lab.
Black = Topics initially in the Blueprint but was later removed.
....1.2.1. VTP Version 1, 2, & 3
....1.2.2. VTP Authentication
....1.2.3. VTP Pruning
....1.2.4. VTP Prune Eligible List
....1.2.5. VTPv3 & Private VLANs
....1.3.1. Static Layer 2 EtherChannels
....1.3.2. PAgP
....1.3.3. LACP
....1.3.4. Layer 3 EtherChannel
....1.3.5. EtherChannel Load Balancing
....1.3.6. EtherChannel Protocol Limiting
....1.3.7. EtherChannel Misconfig Guard
....1.4.1. PVST+
......1.4.1.1. STP Root Bridge Election
......1.4.1.2. STP Path Selection with Port Cost
......1.4.1.3. STP Path Selection with Port Priority
......1.4.1.4. STP Convergence Timers
....1.4.2. Optional STP Features 1.4.2.1. PortFast
......1.4.2.2. UplinkFast
......1.4.2.3. BackboneFast
......1.4.2.4. BPDU Guard
......1.4.2.5. BPDU Filter
......1.4.2.6. Root Guard
....1.4.3. Rapid-PVST+
......1.4.3.1. RSTP Convergence Optimizations
......1.4.3.2. Edge Ports
....1.4.4. Multiple STP
......1.4.4.1. MST Root Bridge Election
......1.4.4.2. MST Path Selection with Port Cost
......1.4.4.3. MST Path Selection with Port Priority
......1.4.4.4. MST and CST/PVST+ Interoperability
......1.4.4.5. Multi-Region MST
....1.5.1. L2 Protocol Tunneling
....1.5.2. Layer 2 MTU
....1.5.3. EtherChannel over 802.1q Tunneling
Last edited by daniel.larsson on Fri May 15, 2015 12:38 pm; edited 10 times in total
 Layer 2 - VLANs (Trunk-ports, Access-ports, Normal VLANs, Extended VLANs)
Layer 2 - VLANs (Trunk-ports, Access-ports, Normal VLANs, Extended VLANs)
Layer 2
Technology: Trunk-ports, Access-ports, Normal VLANs, Extended VLANs
Learned:
-With a Native VLAN-mismatch on a Trunk-port the port becomes in a "port inconsistent state" by STP. However the command "show ip interfaces brief" will show the interfaces as up/up!
Note to self: I was already very strong with Layer 2 technologies and configuration before doing these labs so the time required was minimum. Probably requires minimum review of these labs before exam!
Time required: 45 minutes.
Technology: Trunk-ports, Access-ports, Normal VLANs, Extended VLANs
- Read through L2 Configuration and technology explanations of VLAN:s.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swvlan.html
Learned:
-Only 128 instances of STP can exist on a single switch. Meaning that in essence if running PVST or PVST+ only a total of 128 VLAN:s can be active and forward traffic. This is a limitation of the platform of the 3750X switch. And you are not tested on platform-specific topics for CCIE, however it is worth noting that there is a limit of Spanning-Tree instances on each switch. In this case it happened to be 128 instances of STP.-Adding an additional VLAN when the maximum supported STP-instances is already met will create the VLAN local to that switch that is not running Spanning-Tree. If that VLAN is also allowed on the Trunk-port it can create a loop in the network. Any other VTP-device in the network running in Server-mode can create and propagate this VLAN to a device with STP-limit reached.
-Several parameters for any VLAN can be configured. Such as VLAN-type, VLAN-state, MTU for the VLAN, Spanning-Tree type and so on. For complete reference to these, see the command-reference guide.
-It's impossible to migrate from VTP-version 3 to Version 1 or 2 if Extended VLAN:s (1006-4094) are currently in use.
-Each routed port (SVI's) on the switch creates an internal Extended VLAN to use for the routed port. This internal VLAN is created in the lower end of the Extended VLAN-range, starting at 1006 by default. If SVI's are used they will use an internal Extended VLAN-id, you can't use the same Extended VLAN-id for your network. Check first with command: show vlan internal-usage, or simply create Extended VLAN:s from the top-range (4094) and downwards.
-It's possible to remove VLAN 1 from the allowed VLANs on the trunk link. This is known as the terminology "VLAN 1 minimization". Which means that only management and control-traffic will be allowed in VLAN 1.
-Every trunk-port has a list which tells it which specific VLAN:s are allowed to be pruned from the trunk-link by using VTP. It's called the VLAN Pruning-Eligable list. It's configured on a per-trunk-port basis. This list configures which VLAN:s VTP can prune from the trunk-links!
-A dynamic Access-port using VMPS (Dynamic VLAN-assignment) can belong to only one VLAN at the same time and has a limit of supporting maximum of 20 MAC-addresses per port.
Time required: 1½ hour. - Watched the INE CCIE Videos about VLAN:s.
Time required: 1½ hour. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-Layer 2 Access Switchports page 21.
-Layer 2 Dynamic Switchports page 24.
-802.1Q Dynamic Trunking page 30.
-802.1Q Native VLAN page 33.
-DTP Negotiation page 37.
Learned:
-With a Native VLAN-mismatch on a Trunk-port the port becomes in a "port inconsistent state" by STP. However the command "show ip interfaces brief" will show the interfaces as up/up!
Note to self: I was already very strong with Layer 2 technologies and configuration before doing these labs so the time required was minimum. Probably requires minimum review of these labs before exam!
Time required: 45 minutes.
 Layer 2 - Vlan Trunking Protocol (VTP)
Layer 2 - Vlan Trunking Protocol (VTP)
Layer 2
Technology: Vlan Trunking Protocol - VTP
Learned:
-To use the command "show interface pruning" to see which VLAN:s was requested by the VTP-pruning features. In other words which VLAN:s should not be pruned becuase the neighboring switch requests that these VLAN:s should be forwarded.
Note to self: There are quite a lot to VTP that you normally don't run into. There is a new version 3 that is in the Blueprint that I have minor experience with and needs to address in depth. I feel very Confident with Version 1 and Version 2, but requires more practice with Version 3. These labs only focused on Version 1 and 2 so there is still a lot left with VTP.
I came into these labs feeling extremely confident with VTP, and I was, so there should be needed minimal review before the lab. One thing that i spent a lot of time doing with these labs was troubleshooting VTP.
I don't know if it was intentional by INE or not, but they were all different versions and had very big issues with enabling Pruning on the server and have it propagating across all other switches correctly. What i did to correct it was look at which was the server, and then do a "vtp mode transparent" on all switches, followed by "vtp version 2" followed by "vtp mode client, vtp mode server" respectively. That solved all the issues with these labs. Something to look out for if I decide to do them again.
Note to self 2: I only had issues using the INE Rackrental, cabling this up with my own devices using the same configs had no issues at all and all labs were done in 15-20 min with no VTP-issues!
Time required: 1 hour.
Technology: Vlan Trunking Protocol - VTP
- Read through L2 Configuration and technology explanations of VTP.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swvtp.html
Learned:
-The default VTP-mode is Server, however since VTP-Server saves changes to the NVRAM it will fallback to VTP-Client mode if there are errors with the NVRAM. It will then stay in Client-mode until the NVRAM is working again.
-VTP v3 saves VLAN-information to NVRAM in client mode. However VTP v1 & v2 does not.
-VTP mode off - works the same as VTP-Transparent mode except it does not forward any VTP-advertisements.
-VTP Version 2: There is no Consistency check when a VTP-advertisement is received. It only checks the MD5-checksum and if it's correct the VTP-advertisment is accepted. Consistency check is only performed when adding new information through CLI or SNMP.
-VTP Version 3: Authentication is supported with a hidden key or a secret key. If using the hidden key the password must be provided when doing a primary-server takeover. If using the secret key, you can directly configure the secret key for VTP authentication.
-VTP Version 3: VTP pruning only works for VLANs 1 to 1005, even in VTP v3.
-VTP Version 3: vtp version 3, vtp mode server, will not make it a primary server. By just configuring the switch as a VTP Server it will become a secondary-server and will not be allowed to update VLAN information. To be able to create VLAN:s a takover must be executed from privilege EXEC mode. Run the command: vtp primary to do a takeover, and provide the password if authentication is used in combination with the hidden-password.
-VTP Version 3: VTP v3 separates configuration for Spanning-tree (like MST) and VLAN and you can manually configure each feature as either a Client or a Server.
-VTP Version 3: It's possible to completely turn off VTP in v3. Go to the interface and disable vtp with the command: no vtp. However you can't turn off MST and leave VLAN on for the same port.
-VTP pruning should always be turned off if a transparent switch is used in the network. VTP Pruning is not designed to work with Transparent configured switches. A workaround is to configure every VLAN upstream from the transparent switch as "VLAN pruning-ineligable". This is to make sure that no VLAN:s are pruned that belongs upstream from the VTP Transparent switch.
-If using VTP Server in a Switch-stack then a VTP server takeover with the new stack-masters MAC-address will be executed to become the new VTP-server. The MAC-address is used as the Primary Device ID and can be configured to be persisent: stack-mac persistent timer x. This configuration sets a timer before the stack does a VTP Server takeover with the new stack-master.
-A switch running VTP v1 that receives a VTP advertisment from a VTP v3 switch will then automatically update it's VTP version to 2. In other words, if a Version 3 switch is running in the network the lowest supported version will always be 2 since all switches that receives the V3 advertisment will be updated to version 2 mode.
-A VTP v3 trunk-port will only fallback to VTP v2 if it FIRST receives a VTP v2 advertisement. A VTPv3 trunk-port will send a down-scaled version of the VTP advertisments to the neighboring VTP v2-switch so that the VTP v2 switch can update it's VLAN-database.
-If a VTPv3 switch detects a VTPv2 neighbor over a trunk-port it will send both VTPv2 and VTPv3 advertisements to support both versions. In other words it does not turn off VTPv3 even if it sends down-scaled VTPv2 advertisements over the same trunk!
-VTP Version 3: To enable version 3 it must be manually configured on each switch as compared to version 2 which is advertised using VTP if configured on a server.
-VTP pruning works differently in Version 3 than version 2. In version 2 it is advertised to other switches so you only need to enable VTP Pruning on a server somewhere in the domain. In version 3 it's required to manually configure VTP Pruning on every switch.
Time required: 1 hour. - Watched the INE CCIE Videos about VTP.
Time required: 2 hours. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-VTP Domain page 42.
-VTP Transparent page 48.
-VTP Pruning page 53.
-VTP Version 3 page 212.
Learned:
-To use the command "show interface pruning" to see which VLAN:s was requested by the VTP-pruning features. In other words which VLAN:s should not be pruned becuase the neighboring switch requests that these VLAN:s should be forwarded.
Note to self: There are quite a lot to VTP that you normally don't run into. There is a new version 3 that is in the Blueprint that I have minor experience with and needs to address in depth. I feel very Confident with Version 1 and Version 2, but requires more practice with Version 3. These labs only focused on Version 1 and 2 so there is still a lot left with VTP.
I came into these labs feeling extremely confident with VTP, and I was, so there should be needed minimal review before the lab. One thing that i spent a lot of time doing with these labs was troubleshooting VTP.
I don't know if it was intentional by INE or not, but they were all different versions and had very big issues with enabling Pruning on the server and have it propagating across all other switches correctly. What i did to correct it was look at which was the server, and then do a "vtp mode transparent" on all switches, followed by "vtp version 2" followed by "vtp mode client, vtp mode server" respectively. That solved all the issues with these labs. Something to look out for if I decide to do them again.
Note to self 2: I only had issues using the INE Rackrental, cabling this up with my own devices using the same configs had no issues at all and all labs were done in 15-20 min with no VTP-issues!
Time required: 1 hour.
Last edited by daniel.larsson on Tue May 12, 2015 12:04 pm; edited 2 times in total
 Layer 2/3 - EtherChannels (with PAgP , LAcP, and without negotiations)
Layer 2/3 - EtherChannels (with PAgP , LAcP, and without negotiations)
Layer 2
Technology: Layer 2/3 EtherChannels (with PAgP , LAcP, and without negotiations)
Learned:
-To think in a structural manner with EtherChannels. First check if the channel is formed with "show etherchannel summary". Then check if the trunk was formed with "show interfaces trunk". And lastly check if spanning-tree is forwarding out the correct interface with "show spanning-tree vlan x". I need to remember that the end-goal with EtherChannels is to provide one logical interface for STP instead of viewing it as a loadbalancing protocol.
-Configuring the port-channel interface will make the physical interfaces inherit the configuration of the port-channel interface.
-Ultimately when configuring port-channels/EtherChannels you have to remember to configure them in the correct order:
For Layer 2 - put the physical interfaces in the port-channel/channel-group then configure the port-channel interface and the configuration will be inherited by the physical interfaces.
For Layer 3 - very important! First configure the physical interfaces with "no switchport" THEN add them to the channel-group THEN configure the port-channel interface. Otherwise the channel-group will be considered a Layer 2 interface and can't be re-configured into a layer 3 interface!
-As with SVI 's the ip-address used by the port-channel interface will take up an internal-vlan slot as ben be verified with "show vlan internal usage".
-The Layer 2 interfaces that you configure with "no switchport" command will also always take up an internal vlan. This can be verified with "show vlan internal usage". In other words, if you assign two layer 2 interfaces into a port-channel 3 internal vlans will be used. Two for the physical interfaces and one for the port-channel interface.
Note to self: As with the VTP-labs i struggled a lot with INE's Rackrental configurations. If I'm doing these labs again i will just shutdown interfaces "fa0/19-24" on all switches and do my configurations before bringing them back up.
I feel very confident with PAgP, LAcP or EtherChannels in general. I spent most of my time with these labs troubleshooting topics outside the scope of EtherChannels...such as "stp misconfiguration" on etherchannels (where one side is in a bundle and the other is not, so STP EtherChannel Guard blocks this).
In my physical lab of only 3560's and a 3750 this did not happen and the labs went smooth and easy as expected.
I probably need very little review of these topics other than to "get it in the back of my head" in which order to configure Layer 2 vs Layer 3 to not have to re-do them on the lab exam!
Time required: 1½ hours.
Technology: Layer 2/3 EtherChannels (with PAgP , LAcP, and without negotiations)
- Read through L2 Configuration and technology explanations of Etherchannels.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swethchl.html
Learned:
-Inbound broadcasts or multicast packets on one link is automatically blocked from returning on any other link in the EtherChannel.
-DTP and CDP packets run over the physical ports even if they are bundled into an EtherChannel. They run over the lowest numbered VLAN (1 usually).
-The MAC-address of the etherchannel is taken by the first port that comes up (L2) or the Stack-Master as soon as the interface is created with the port-channel command. (L3)
-Spanning-Tree loops can occur if you configure an EtherChannel in the "on" mode due to no PAgP negotiations are performed that can result in one end of the channel being allowed to send packets while the other end is not part of the EtherChannel.
-Always manually choose the correct load-balancing configuration depending on your network topology. Think of a two-way traffic traffic pattern. You may need one load-balancing setting for the outbound traffic, and another from the inbound-path. For example: 4 different hosts communicating with the same router could be using source-ip address as load-balancing when communicating with the router. The router needs to be configured to use destination-ip address to load-balance across the Etherchannel when sending traffic back to the hosts.
-Stacking two switches that have EtherChannels configured between them will result in a self-looped scenario that STP will detect and correct. (A stack merge) The PAgP/LAcP configuration of the winning Switch will be saved in NVRAM. The loosing switch will have it's PAgP/LAcP configuration removed.
-With LAcP if a new Stack Member is elected the LAcP system-id will change and cause a STP-reconvergence becuase the EtherChannel will flap to reflect the new system-id. A workaround for this is to manually set the MAC-persistant timer: stack-mac persistent timer.
-It's possible to manually change the spanning-tree path-cost of the physical interfaces in the EtherChannel group. This will not bring the EtherChannel down but can result in unexpected behaviour with Spanning-Tree forwarding path.
-Link-State tracking is a method used to enable NIC-Teaming on servers to provide redundancy over EtherChannels using a Primary port-group and a Secondary port-group. The terminology Downstream refers to the physical links towards the Servers. Upstream refers to the physical links towards the Distribution layer switches. Link-State Tracking is used to tell the Servers using NIC-Teaming which interfaces to use to forward traffic.
Time required: 1 hour. - Watched the INE CCIE Videos about EtherChannels.
Time required: 2 hours. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-Layer 2 EtherChannel page 60.
-Layer 2 EtherChannel with PAgP page 66.
-Layer 2 EtherChannel with LAcP page 74.
-Layer 3 EtherChannel page 82.
Learned:
-To think in a structural manner with EtherChannels. First check if the channel is formed with "show etherchannel summary". Then check if the trunk was formed with "show interfaces trunk". And lastly check if spanning-tree is forwarding out the correct interface with "show spanning-tree vlan x". I need to remember that the end-goal with EtherChannels is to provide one logical interface for STP instead of viewing it as a loadbalancing protocol.
-Configuring the port-channel interface will make the physical interfaces inherit the configuration of the port-channel interface.
-Ultimately when configuring port-channels/EtherChannels you have to remember to configure them in the correct order:
For Layer 2 - put the physical interfaces in the port-channel/channel-group then configure the port-channel interface and the configuration will be inherited by the physical interfaces.
For Layer 3 - very important! First configure the physical interfaces with "no switchport" THEN add them to the channel-group THEN configure the port-channel interface. Otherwise the channel-group will be considered a Layer 2 interface and can't be re-configured into a layer 3 interface!
-As with SVI 's the ip-address used by the port-channel interface will take up an internal-vlan slot as ben be verified with "show vlan internal usage".
-The Layer 2 interfaces that you configure with "no switchport" command will also always take up an internal vlan. This can be verified with "show vlan internal usage". In other words, if you assign two layer 2 interfaces into a port-channel 3 internal vlans will be used. Two for the physical interfaces and one for the port-channel interface.
Note to self: As with the VTP-labs i struggled a lot with INE's Rackrental configurations. If I'm doing these labs again i will just shutdown interfaces "fa0/19-24" on all switches and do my configurations before bringing them back up.
I feel very confident with PAgP, LAcP or EtherChannels in general. I spent most of my time with these labs troubleshooting topics outside the scope of EtherChannels...such as "stp misconfiguration" on etherchannels (where one side is in a bundle and the other is not, so STP EtherChannel Guard blocks this).
In my physical lab of only 3560's and a 3750 this did not happen and the labs went smooth and easy as expected.
I probably need very little review of these topics other than to "get it in the back of my head" in which order to configure Layer 2 vs Layer 3 to not have to re-do them on the lab exam!
Time required: 1½ hours.
 Spanning-Tree (CST, PVST+, RPVST+ or 802.1D)
Spanning-Tree (CST, PVST+, RPVST+ or 802.1D)
Layer 2
Technology: Spanning-Tree (CST, PVST+, RPVST+ or 802.1D)
Learned:
-In general it's best to always check the current STP-forwarding path before doing any STP-changes. Check with "show spanning-tree vlan x" from the "edge" of the network towards the root-bridge before modyfing STP-values. The reason is that STP may not forward as expected for many reason beyond your control.
-With multiple uplinks and downlinks between switches, STP will always choose the root-port as the lowest numbered port-id since everything match. However if you want to keep the STP path-cost unmodified you have to adjust the port-priority of the designated bridge. In other words the upstream bridge and not the local bridge. Because the port-priority is a designated value, in other words it's advertised downstream NOT upstream!
-If you get a configuration task that asks you to manually set STP timers be sure to know the default timers of: hello-time 2 seconds, forward-time 15 seconds, max-age 20 seconds.
Because you would have to know the default timers if they tell you to wait x amount of seconds before a port is forwarding.
-STP Max Age can also be referred to as a STP Configuration message. Since if this timer expires the switch will flood all MAC-addresses to re-learn.
Note to self: Overall i feel extremely confident with Legacy STP but i should probably just re-do these labs to learn all the commands and get familiar with the odd way of expressing how you should configure the STP-issues. I configured each lab in less then 5 minutes easily but i spent a lot of time troubleshooting other issues outside the scope of STP. Such as VTP again, which is a standard config in the INE CCIE RSv5 workbook. All labs suffer from it.
The problem: They run two switches with ios release 15.0 where a bug is fixed, SW1 and SW2 never has a problem getting VTP advertisements from VTP Server SW1.
SW3 and SW4 are running older IOS-versions of 12.2 where there is a nasty bug with VTP checksums not calculated correctly - or not even working at all.
The solution: go to the VTP-server (sw1) and create a bogus vlan, 999, exit it and delete that vlan to create VTP advertisements. Hopefully SW3 and SW4 will get these. If they don't, go to vtp server and change domain name and set a password. Then configure these on SW2-4. Then create a bogus vlan and delete it on VTP-server.
As a matter of fact, this has become my number one thing to start with in the INE Racks as it just saves me more time to always do it then forget it.
Time required: 1 hour.
Technology: Spanning-Tree (CST, PVST+, RPVST+ or 802.1D)
- Read through Configuration and technology explanations of Basic Spanning-Tree:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960x/software/15-0_2_EX/layer2/configuration_guide/b_lay2_152ex_2960-x_cg/b_lay2_152ex_2960-x_cg_chapter_0110.html#topic_253E71B60D51407C94A7983C910490A2
Learned:
-Trying to make a switch the root-bridge with the command spanning-tree vlan x root primary will fail if the required priority is less then 1.
-In a network where there are switches that both support and not support the Extended VLAN/System-ID field the switches with the Extended VLAN support will most likely not be elected as a root-bridge due to the VLAN-number being added to the priority of the switch.
-The BPDU's that are sent between switches carries information about the SENDING switch so that the RECEIVING switch can make a decision. Not the other way around!
-STP-keepalives are sent on every interface except SFP-slots.
-Increase the port-priority (configure a lower priority) to make a switch elect it as a prefered root-port. The lowest port-priority is likely to become the root-port.
-Lower the path-cost (configure a lower path-cost) of an interface to make a switch elect it as a prefered root-port or designated-port.
-The IEEE 802.1D standard specifies that rhere are 17 multicast addresses assigned for different bridge-protoculs (such as spanning-tree). The addresses are ranging from 0x00180C2000000 to 0x0180C2000010. These addresses are static addresses that cannot be removed.
-Regardless of the spanning-tree state, each switch in the stack receives but does not forward packets destined for addresses between 0x0180C2000000 and 0x0180C200000F.
-If spanning tree is enabled, the CPU on the switch or on each switch in the stack receives packets destined for 0x0180C2000000 and 0x0180C2000010. If spanning tree is disabled, the switch or each switch in the stack forwards those packets as unknown multicast addresses.
-The IEEE 802.1Q trunking standard defines that only ONE VLAN is used on trunk links, however the Cisco devices will run PVST+ or RPVST+. This is not a problem, but a non-cisco device will probably run their 802.1Q port as defined by the standard. In that case the cisco switch/end of the trunk will revert back to either PVST+ or RPVST+ and maintain one spanning-tree instance per vlan on the Cisco-side of the network!
-The number of BPDU's that can be sent before pausing 1 second can be configured with the command: spanning-tree transmit hold-count x.
Easy way to calculate root port with default timers: Always pick the closest port to the root as the Root-port. If multiple ports are connected to the same switch it will always pick the lowest port-number as the root-port!
Time required: 1 hour. - Watched the INE CCIE Videos about Basic Spanning-Tree / Legacy Spanning-Tree.
Time required: 1 hour. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-STP Root Bridge Election page 86.
-STP Path Selection with Port Cost page 93.
-STP Path Selection with Port Priority page 97.
-Tuning STP Convergence Timers Page 102.
Learned:
-In general it's best to always check the current STP-forwarding path before doing any STP-changes. Check with "show spanning-tree vlan x" from the "edge" of the network towards the root-bridge before modyfing STP-values. The reason is that STP may not forward as expected for many reason beyond your control.
-With multiple uplinks and downlinks between switches, STP will always choose the root-port as the lowest numbered port-id since everything match. However if you want to keep the STP path-cost unmodified you have to adjust the port-priority of the designated bridge. In other words the upstream bridge and not the local bridge. Because the port-priority is a designated value, in other words it's advertised downstream NOT upstream!
-If you get a configuration task that asks you to manually set STP timers be sure to know the default timers of: hello-time 2 seconds, forward-time 15 seconds, max-age 20 seconds.
Because you would have to know the default timers if they tell you to wait x amount of seconds before a port is forwarding.
-STP Max Age can also be referred to as a STP Configuration message. Since if this timer expires the switch will flood all MAC-addresses to re-learn.
Note to self: Overall i feel extremely confident with Legacy STP but i should probably just re-do these labs to learn all the commands and get familiar with the odd way of expressing how you should configure the STP-issues. I configured each lab in less then 5 minutes easily but i spent a lot of time troubleshooting other issues outside the scope of STP. Such as VTP again, which is a standard config in the INE CCIE RSv5 workbook. All labs suffer from it.
The problem: They run two switches with ios release 15.0 where a bug is fixed, SW1 and SW2 never has a problem getting VTP advertisements from VTP Server SW1.
SW3 and SW4 are running older IOS-versions of 12.2 where there is a nasty bug with VTP checksums not calculated correctly - or not even working at all.
The solution: go to the VTP-server (sw1) and create a bogus vlan, 999, exit it and delete that vlan to create VTP advertisements. Hopefully SW3 and SW4 will get these. If they don't, go to vtp server and change domain name and set a password. Then configure these on SW2-4. Then create a bogus vlan and delete it on VTP-server.
As a matter of fact, this has become my number one thing to start with in the INE Racks as it just saves me more time to always do it then forget it.
Time required: 1 hour.
 Spanning-Tree Optional Features (PortFast, BPDU Guard, BPDU Filter, Uplink Fast, Backbone Fast) & UDLD
Spanning-Tree Optional Features (PortFast, BPDU Guard, BPDU Filter, Uplink Fast, Backbone Fast) & UDLD
Layer 2
Technology: Spanning-Tree Optional Features (PortFast, BPDU Guard, BPDU Filter, Uplink Fast, Backbone Fast) & UDLD
Learned:
-Exactly how important it is to configure the trunk-port as a "portfast trunk" port, and not a regular portfast port. Since a cisco switch runs PVST by default the "portfast trunk" command is needed on trunk ports to enable the portfast feature for all the VLAN instances.
-Use the "show spanning-tree interface fa0/x portfast" and "show spanning-tree interface fa0/x detail" to quickly figure out if BPDU's are being sent or received on the interface.
-Use the "default" global configuration command to quickly reset configurations to the default values. For example "default interface range fa0/19-24" will reset the interfaces to default config. "default spanning-tree vlan 1-4094 priority" will reset the priority for all the VLAN:s on the switch.
-UplinkFast requires default STP-priorities to work, and when enabled automatically adjusts the default priority to 49152 and the port-cost to 3000. This is to avoid it from becoming a transit-switch for STP.
-BackboneFast when enabled in the entire STP-domain, will send RLQ (Root Link Queries) out all non-designated ports and ask if any other switch knows where the root-bridge is. Based on the query replies the new root-port is elected. It will still transition through the normal listenint/leraning/forwarding states but it won't have to wait for the max_age timer to expire!
-BPDU Guard is configured differently in "global mode" compared to "interface mode". It's strangely located under the "portfast" command in global mode. The command in global is "spanning-tree portfast bpduguard default" and in interface mode "spanning-tree bpduguard enable". This is because in "global mode" it's only enabled on "portfast" ports (STP edge ports).
-BPDU filter WORKS differently depending on where it's configured. In interface mode BPDU filter will completely stop SENDING and RECEIVING BPDU's effectively disabling STP on that port. Configured in "global mode" BPDU filter will revert back to normal STP-operations if it RECEIVED BPDU's but it will still not SEND BPDU's. However it will send out exactly 11 BPDU's as a loop-prevention mechanism to ensure that this is an end-host. Also if configured in global mode it will only be enabled on PortFast interfaces. So if the configuration task says to "ensure that BPDU filter is enabled only on PortFast ports" it means that they ask you to configure BPDU filter globally and not on the interface!
-Root Guard basically prevents a Designated port (downstream interface) from becoming a root-port (upstream interface) by placing that port in a root-inconsistent state until that port stops receiving a superior BPDU.
-Loop Guard basically prevents a Non-Designated (upstream interface) port from becoming a Designated port (downstream interface) by using BPDU's. Configured globally it looks like it's enabled on all UP ports but it will only monitor the Non-designated ports.
-Only Loop Guard or Root Guard can be enabled on an interface. In other words you have to choose to prevent a port from fliping between a downstream to upstream (Root guard) or vice versa (Loop Guard).
-An interesting design to test Loop-Guard, since it works based on BPDU's, is to stop a non-designated port (for example the root-port upstream interface) from receiving any BPDU's. This can be done by using BPDU-filter on the switch for that interface. Since it will then stop to SEND outbound BPDU's AND filter any INBOUND BPDU's Loop Guard will notice that it stop receiving BPDU's on it's Non-Designated port and will then put this port in a "loop inconsistent state". Effectively preventing it from forwarding downstream (Designated port).
-UDLD should be configured combined with Loop Guard to protect against every Unidirectional link failure. UDLD will detect a miswired fiber-pair (TX-toTX and RX-to-RX) while Loop-Guard will be able to detect software failures with STP (although extremely unlikely to happen).
Note to self: I should do these labs again as the final preparations for the Lab exam. These labs by themselves are pretty easy and doesn't take a lot of time to do. But they really do help with remembering the small details and the differences between configuring STP-features Globally or in Interface mode.
I find these labs to be easy, since im confident with L2, but they were good and had me thinking sometimes where a specific command was located in the IOS by the way they worded/specified how to configure the features. All-in-all though, I should not have to study any theory on these topics but rather work on these labs to learn the interface-specific commands faster!
I spent most of my time with these labs learning new commands to quickly re-configure between the modes. Especially the "default" command is very usefull to quickly test these features.
The only downside to all these comprehensive labs are that they are only for Legacy STP and not for RSTP. Any sane person would just type "spanning-tree mode rpvst" as the first command in a new switch.
Time required: 2½hours.
Technology: Spanning-Tree Optional Features (PortFast, BPDU Guard, BPDU Filter, Uplink Fast, Backbone Fast) & UDLD
- Read through Configuration and technology explanations of Optional Spanning-Tree features:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swstpopt.html
Learned:
-Interfaces configured with Port Fast goes through the normal STP-status changes if the switch is rebooted. However when the switch is turned on it bypasses the Listening and the Learning stage and goes directly to the Forwarding-mode.
-BPDU Guard can be enabled globally or on a per interface level - and will affect all Port Fast configured interfaces. In both cases it will shutdown the interface where BPDU's were received and it will put the interfaces in the Err-Disable state.
-BPDU Filter can be enabled globally or on a per interface level - and it will affect all Port Fast configured interfaces. It works differently!
If BPDU Filter is enable Globally it will stop receiving and sending out BPDU's out all ports. However if it detects a BPDU it will disable Port Fast and operate as a standard STP-port.
If BPDU Filter is enabled on an interface it will be the same as disabling Spanning-Tree entirely on that interface. It will not send out or receive any BPDU's on that interface!
-BackboneFast is a feature that is designed to detect in-direct link-failures and works together with UplinkFast to detect in-direct link-failures and transition the root-port immedeiately to the learning state.
-Configuring a Voice VLAN automatically enables PortFast on that interface. However if the voice VLAN is removed it does NOT disable Port Fast!
-Uplink Fast cannot be configured if the Switch is not using the default Spanning-Tree Priority.
-If Root Guard and Uplink Fast is configured on the same interface and the switch is using the Uplink Fast feature to move a new root-port into the learning-state then Root Guard will put the alternate/blocked port into a "root inconsistent state" preventing the new uplink from working becuase there are two active root-ports for a small set of time while Uplink Fast is transitioning the new root-port!
Time required: 1 hour. - Read through Configuration and technology explanations of Unidirectional Link Detection:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swudld.html
Learned:
-UDLD can be used as a heart-beat mechanism over WAN-connections if it's required that the link should go down if it's unhealthy.
-UDLD is a L2 protocol but works with the L1 autoconfiguration protocols. As in it detects faults that the L1 autosignaling would not, such as misconnected fiber pairs.
-UDLD informs it's neighbors to clear it's cache for the link if the port is shutdown, UDLD is disabled or the switch is rebooted. This is done to keep the UDLD cache's in synch over the link.
-In both modes (normal and aggressive) the link is considered undetermined if it's not synchronized. However with aggressive mode it continues to try and bring the link up and if it fails the link is considered unidirectional and will be shutdown.
-As would be expected UDLD can't detect Unidirectional failures if it's connected to another switchport that does not support UDLD. Therfor, always configure it on both sides of the link in the same UDLD mode.
-Configure UDLD globally will only enable it on Fiber-optic ports. If UDLD is needed on other media types it has to be configured in interface-configuration mode.
-If a port is shutdown by UDLD the best way to reenable it is with the command "udld reset".
Time required: 15 minutes. - Watched the INE CCIE Videos about Optional Spanning-Tree features & UDLD.
Time required: 1 hour. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-STP PortFast page 105.
-STP PortFast Default page 110.
-STP UplinkFast page 114.
-STP BackboneFast page 120.
-STP BPDU Guard page 127.
-STP BPDU Guard Default page 133.
-STP BPDU Filter page 137.
-STP BPDU Filter Default page 143.
-STP Root Guard page 149.
-STP Loop Guard page 154.
-Unidirectional Link Detection page 161.
Learned:
-Exactly how important it is to configure the trunk-port as a "portfast trunk" port, and not a regular portfast port. Since a cisco switch runs PVST by default the "portfast trunk" command is needed on trunk ports to enable the portfast feature for all the VLAN instances.
-Use the "show spanning-tree interface fa0/x portfast" and "show spanning-tree interface fa0/x detail" to quickly figure out if BPDU's are being sent or received on the interface.
-Use the "default" global configuration command to quickly reset configurations to the default values. For example "default interface range fa0/19-24" will reset the interfaces to default config. "default spanning-tree vlan 1-4094 priority" will reset the priority for all the VLAN:s on the switch.
-UplinkFast requires default STP-priorities to work, and when enabled automatically adjusts the default priority to 49152 and the port-cost to 3000. This is to avoid it from becoming a transit-switch for STP.
-BackboneFast when enabled in the entire STP-domain, will send RLQ (Root Link Queries) out all non-designated ports and ask if any other switch knows where the root-bridge is. Based on the query replies the new root-port is elected. It will still transition through the normal listenint/leraning/forwarding states but it won't have to wait for the max_age timer to expire!
-BPDU Guard is configured differently in "global mode" compared to "interface mode". It's strangely located under the "portfast" command in global mode. The command in global is "spanning-tree portfast bpduguard default" and in interface mode "spanning-tree bpduguard enable". This is because in "global mode" it's only enabled on "portfast" ports (STP edge ports).
-BPDU filter WORKS differently depending on where it's configured. In interface mode BPDU filter will completely stop SENDING and RECEIVING BPDU's effectively disabling STP on that port. Configured in "global mode" BPDU filter will revert back to normal STP-operations if it RECEIVED BPDU's but it will still not SEND BPDU's. However it will send out exactly 11 BPDU's as a loop-prevention mechanism to ensure that this is an end-host. Also if configured in global mode it will only be enabled on PortFast interfaces. So if the configuration task says to "ensure that BPDU filter is enabled only on PortFast ports" it means that they ask you to configure BPDU filter globally and not on the interface!
-Root Guard basically prevents a Designated port (downstream interface) from becoming a root-port (upstream interface) by placing that port in a root-inconsistent state until that port stops receiving a superior BPDU.
-Loop Guard basically prevents a Non-Designated (upstream interface) port from becoming a Designated port (downstream interface) by using BPDU's. Configured globally it looks like it's enabled on all UP ports but it will only monitor the Non-designated ports.
-Only Loop Guard or Root Guard can be enabled on an interface. In other words you have to choose to prevent a port from fliping between a downstream to upstream (Root guard) or vice versa (Loop Guard).
-An interesting design to test Loop-Guard, since it works based on BPDU's, is to stop a non-designated port (for example the root-port upstream interface) from receiving any BPDU's. This can be done by using BPDU-filter on the switch for that interface. Since it will then stop to SEND outbound BPDU's AND filter any INBOUND BPDU's Loop Guard will notice that it stop receiving BPDU's on it's Non-Designated port and will then put this port in a "loop inconsistent state". Effectively preventing it from forwarding downstream (Designated port).
-UDLD should be configured combined with Loop Guard to protect against every Unidirectional link failure. UDLD will detect a miswired fiber-pair (TX-toTX and RX-to-RX) while Loop-Guard will be able to detect software failures with STP (although extremely unlikely to happen).
Note to self: I should do these labs again as the final preparations for the Lab exam. These labs by themselves are pretty easy and doesn't take a lot of time to do. But they really do help with remembering the small details and the differences between configuring STP-features Globally or in Interface mode.
I find these labs to be easy, since im confident with L2, but they were good and had me thinking sometimes where a specific command was located in the IOS by the way they worded/specified how to configure the features. All-in-all though, I should not have to study any theory on these topics but rather work on these labs to learn the interface-specific commands faster!
I spent most of my time with these labs learning new commands to quickly re-configure between the modes. Especially the "default" command is very usefull to quickly test these features.
The only downside to all these comprehensive labs are that they are only for Legacy STP and not for RSTP. Any sane person would just type "spanning-tree mode rpvst" as the first command in a new switch.
Time required: 2½hours.
 Spanning-Tree (MSTP 802.1s , RSTP 802.1w)
Spanning-Tree (MSTP 802.1s , RSTP 802.1w)
Layer 2
Technology: Spanning-Tree (MSTP 802.1s , RSTP 802.1w)
Learned:
-Not really learned, but worth writing down to memorize once and for all. A MST Region is defined by a number of switches that share the same configuration parameters. Namely MST Name and Revision number. We subdivide the region with STP instances and map VLAN:s to the instances.
-As with normal STP if you are faced with a configuration task to alter the L2-forwarding path for MST-switches just look at the current spanning-tree forwarding path for the specific instance. E.g "show spanning-tree mst 1" and see where the root is.
Check the current STP-cost with "show spanning-tree mst 1 detail" and then follow normal procedure of altering the STP-cost with "spanning-tree mst 1 cost 1000" to alter the forwaridng path.
But be sure to always check the current forwarding path first before altering cost or priority!
-To figure out the total end-to-end path cost use the command "show spanning-tree mst 1 detail" and look at the "designated port cost" and the "local port cost", add them together to get the end-to-end cost. The designated port cost is the upstream bridge, and the local port cost is the local switch.
Note to self: I didn't struggle at all with the configuration of MST given the task assignments. However I will need to go over a few scenarios with MST-configurations to fully understand exactly how it works. I found a very good resource at INE for this...
I will have to read before lab: http://blog.ine.com/2010/02/22/understanding-mstp/
Time required: 3 hours.
Technology: Spanning-Tree (MSTP 802.1s , RSTP 802.1w)
- Read through Configuration and technology explanations of Multiple Spanning-Tree and Rapid Spanning-Tree:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swmstp.html
Learned:
MST
-With MST the only instance that sends and receives BPDU's are the IST instance (Internal Spanning-Tree) which belongs to region 0.
-MST Regions share the same protocol parameters and the same protocol timers, but the instances within each region are independent. For instance MST Instance A in Region A has it's own topology information compared to MST Instance B in Region A but uses the same protocol with the same protocol timers.
-Each MST region will select a Root switch to their Internal Spanning-Tree Instance called the IST Master. When multiple regions are connected together a Common Insternal Spanning-Tree (CIST) root will also be selected in one of the regions based on the common STP-calculations.
-Some odd naming conventions are used by Cisco when using MST. CIST (Common Internal Spanning-Tree) is the Spanning-Tree instance 0 that spans the entire network through all MST Regions.
The CIST instance will elect a CIST Root which is the root-switch for the entire network and all MST Regions. This is the instance 0 that sends and receives BPDUS's between each switch in all MST Regions.
Each region will also elect a root within the region called the IST root. The naming for MST differs between the IEEE Standard, Ciscos PreStandard and the Cisco-standard of MST. This image better explains the terminology differences:
-IST and MST instances uses a hop-count and a path-cost system simular to the IP TTL (Time-to-Live) field when sending BPDU's. If the hop-count reaches 0 the switch that receives the BPDU with hop-count 0 discards that BPDU and ages out the information learned on that port.
-To comply with the standard cisco has kept some of their own standard names and prestandard names. For example the CIST Regional Root-port is refered in Cisco documentation as the "Boundary" port and will also be displayed as a "boundary" port in the show-commands.
-MST is backwards-compatible with 802.1D (legacy STP). If it detects BPDU's for 802.1D on a port it will convert to running 802.1D on that port automatically. However it doesn't auto-revert back to running MST or RSTP if the legacy switch is removed and the legacy BPDU's is not received. A protocol-migration needs to be done in this case with the command:
clear spanning-tree detected-protocols
RSTP
-An image that explains the different port roles and if they're active in the topology or not. A comparison between legacy STP and RSTP:
-With RSTP a handshake procedure is done before transitioning to the forwarding state. If a switch receives a BPDU with a lower switch priority and agrees to that configuration change a BPDU is sent back over that port with the agreement flag set. This port then becomes the new root-port and every non-edge port (every port not specifically configured with PortFast) will be put in the blocking stage to prevent a switch loop.
This image explains the process: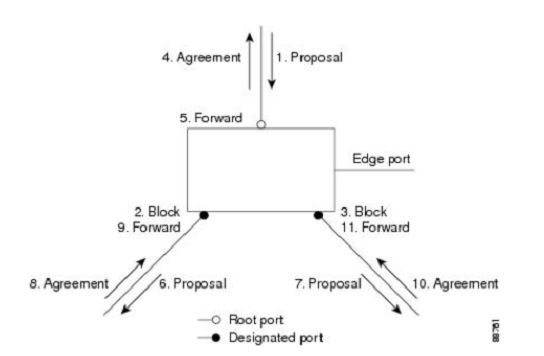
-MST Boundary ports is likely to be needing manual tuning if it connects to a PVST+ or RPVST+ cloud. All MST boundary ports needs to be in the forwarding state to achieve load-balancing, and if the boundary ports connects to a non MST-cloud manual tuning may be needed to make sure that all the MST boundary ports are actively forwarding.
-Cisco's recommendation is to not use plenty of MST-regions, but instead use a L3-device to segment the network into smaller LAN:s each containing a small number of MST-regions.
-RSTP transitions to the forwarding state immediately over point-to-point links (a switchport that connects directly to another switchport). RSTP assumes that it's a point-to-point link based on the speed and duplex settings on the port. A link is considered a point-to-point link if it's in full-duplex mode.
This means that if you have a switch-to-switch link that for some reason is in a half-duplex mode you need to manually configure it as a spanning-tree point-to-point link for it to transition quickly to the forwarding state.
-If a network runs with devices that both supports Cisco prestandard and Cisco standard MST it's required to manually configure each interface as the correct neighbor type for MST to work properly.
Time required: 2 hours. - Watched the INE CCIE Videos about Rapid Spanning-Tree and Multiple Spanning-Tree (RSTP & MST).
Time required: 2 hours. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-MST Root Bridge Election page 164.
-MST Path Selection with Port Cost page 171.
-MST Path Selection with Port Priority page 175.
-MST and Rapid Spanning Tree page 179.
Learned:
-Not really learned, but worth writing down to memorize once and for all. A MST Region is defined by a number of switches that share the same configuration parameters. Namely MST Name and Revision number. We subdivide the region with STP instances and map VLAN:s to the instances.
-As with normal STP if you are faced with a configuration task to alter the L2-forwarding path for MST-switches just look at the current spanning-tree forwarding path for the specific instance. E.g "show spanning-tree mst 1" and see where the root is.
Check the current STP-cost with "show spanning-tree mst 1 detail" and then follow normal procedure of altering the STP-cost with "spanning-tree mst 1 cost 1000" to alter the forwaridng path.
But be sure to always check the current forwarding path first before altering cost or priority!
-To figure out the total end-to-end path cost use the command "show spanning-tree mst 1 detail" and look at the "designated port cost" and the "local port cost", add them together to get the end-to-end cost. The designated port cost is the upstream bridge, and the local port cost is the local switch.
Note to self: I didn't struggle at all with the configuration of MST given the task assignments. However I will need to go over a few scenarios with MST-configurations to fully understand exactly how it works. I found a very good resource at INE for this...
I will have to read before lab: http://blog.ine.com/2010/02/22/understanding-mstp/
Time required: 3 hours.
Last edited by daniel.larsson on Tue May 12, 2015 12:03 pm; edited 2 times in total
 Configuring Fallback Bridging
Configuring Fallback Bridging
Layer 2
Technology: Configuring Fallback Bridging
Technology: Configuring Fallback Bridging
- Read through Configuration and technology explanations of Configuring Fallback Bridging and protected ports
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swfallbk.html#marker-1035383
Learned:
-Fallbackbridging should not ever be configured with a switch that uses Private VLAN:s.
-Fallback Bridging is basically taking a bunch of switchports and put them in the same bridge. Remember that every switch-port as a build-int bridge. So what the fallback bridging does is group multiple bridges in the same group. It bridges your bridges (switchports) so to speak. Do not mistake this for a VLAN which logically groups ports in layer 2.
Remember the core topics of what a bridge does! It learns MAC-addresses and populates the CAM-table! So by grouping multiple interfaces into a single bridge they will be considered a single bridge and not multiple bridges!
This means that you Can actually bridge-ports that belong to different VLANS and even routed ports into the same bridge-group and they will still be able to communicate because of how a bridge works. This is because all switch-ports are a single-bridge now and that bridge will learn where the MAC-addresses are located. Do note though that it doesn't mean that in this case we could ping between a host in vlan 10 and subnet 10.0.0.0/24 and a host in vlan 20 and subnet 20.0.0.0/24.
Although they are in the same bridgegroup they are still in different subnets and in different VLAN:s so they are still logically separated at L2. But the source and destination MAC-addresses would not be learned on a per-switch-port basis because technically we have reconfigured this to a single bridge instead of multiple bridges.
It is worth noting that the broadcasts can not be seen between the different VLAN:s configured as they still work and separate traffic at Layer 2. But the bridge in this case consists of all ports where all VLAN:s inside that bridge belongs.
-Fallback Bridging does not work with Protected ports.
Time required: 1 hour. - There are no INE CCIE Videos about Fallback bridging and there are no specific labs regarding Fallback bridging. It's a very small topic in the blueprint so i will take a guess that the theory will be enough for the Lab!
Note to self: The only thing i will have to remember about this topic is if you are met with a design requirement that specifically tells you to enable communication for non IP-protocols in a design with multiple vlans and subnets. For example to enable IPX-traffic for hosts in multiple parts of the switch.
 Configuring Port-Based Traffic Control (Protected Ports, Storm Control, Port Security, Blocked Ports) & MAC-address table static entries and aging
Configuring Port-Based Traffic Control (Protected Ports, Storm Control, Port Security, Blocked Ports) & MAC-address table static entries and aging
Layer 2
Technology: Configuring Port-Based Traffic Control (Protected Ports, Storm Control, Port Security, Blocked Ports) & MAC-address table static entries and aging
Configuring Port-Based Traffic Control
Learned:
-Normally MAC-addresses are populated and learned dynamically so when configured manually they don't age out. This can be used simular to the "blackhole routing to null interface". Just create a static MAC-table entry that points towards an interface that is not in use and all traffic is silently droped because it points to an interface that's not in use.
Note to self: There isn't much to Storm Control and I won't have to re-do that lab before the Lab exam. However I need to pay attention to what the task says, if the task says to assign Storm Control using a relative percentage of the interface bandwidth it just means to check the interface bandwidth and set the level.
The MAC-Address Table Static Entries is more difficult. But i don't need to re-do that lab before the Lab Exam. I feel confident that if I'm given a task to configure static MAC-entries i will solve it. I just have to look out for the words used for the task!
If given an assignment that static entries would solve, just check the interface with the command "show int fa0/x" to get the BIA so you can do the MAC-address table entry. I have to remember to use the BIA-address on the switch that requires the MAC-routing.
Time required: 30 minutes.
Technology: Configuring Port-Based Traffic Control (Protected Ports, Storm Control, Port Security, Blocked Ports) & MAC-address table static entries and aging
Configuring Port-Based Traffic Control
- Read through Configuration and technology explanations of Configuring Port-Based Traffic Control.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swtrafc.html#marker-1135324
Learned:
-If a threshold for Multicast is configured and reached it will block all non-control multicast traffic. BPDU's and CDP will still run for example, but OSPF, EIGRP and RIP sends multicast traffic so they will stop working!
-The default interval for traffic controlled is a meassure of 1 second. IF the threshold is exceeded during this time-period, the next time-period will block that specific traffic. An image better explains how it works in this case:
-Protected ports only block communication between another protected port. So to isolate ports at L2 they must both be configured as protected ports. A non-protected port can communicate with a protected port through normal procedures.
For two protected ports to communicate with each other they must go through a L3 device first. They are protcted from Unicast, Multicast (except PIM control messages) and Broadcasts at L2.
-As could be expected a stacked switch is represented as a logical single switch so a protected port in S1 will not communicate with a protected port in S2 even if they are separate physical switches - when stacked they are logically one single switch.
-Do combine Protected ports with Private-VLAN ports. Even though there are some combinations that works it's recommended to never combine them.
-Port Blocking is a feature that works in combination with Protected ports that will block Unknown unicast (only Frames/L2 traffic) flooding from the switch. This is to make sure that anyone communicating with the protected port at L2 should already have it's L2 address.
-If port-security is used with secure MAC-addresses that is learned dynamically or configured statically on the port, a violation occurs on that port if any other MAC-address tries to communicate through that port.
However it ALSO monitors so that if this secure MAC-address tries to come in at another secure-port a violation also occurs. It makes sense afterall, if the switch knows where a secure MAC-address is located it should be sourced from that port and not from another port.
For example:
port 1 is has learned the secure mac address of 0000.0000.0001 .
port 2 a host is trying to use mac address of 0000.0000.0001 on this port,, Port-Security detects this even if it may not be a direct violation of port 2 security configuration it should not belong in port 2 when it was learned in port 1.
CAUTION! This violation only occurs if that MAC-address is seen within the same VLAN!
-Port Security: MAC-addresses will be learned dynamically by default, this means that when the switch reboots it looses the configuration and has to re-learn the MAC-addresses. Configure them statically to save it to the running-config.
-Port security: Do not configure "protected mode" on a trunk port. The reason is that you will not be notified when any VLAN:s on the trunk have reached it's maximum number of learned MAC-addresses even if the physical port has not reached it's limit!
-Port Security: The different modes that can be configured works differently and can be difficult to remember. This image better explains all the variations: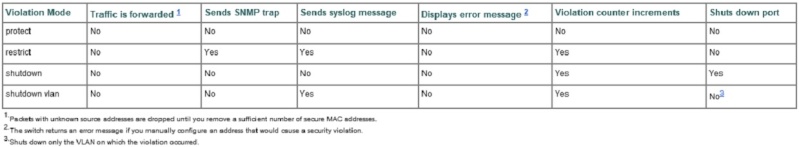
-Port Security: As can be expected, if you use VoIP and have an IP-phone connected to the port when you enable switchport port-security, make sure to change the maximum allowed MAC-addresses to two. One for the phone and one for the PC. If multiple PC's are connected to the internal phone-switch the port-security max MAC-addresses also needs to be configured to suppor tthis.
-Port Security: If you increase the maximum allowed MAC-addresses on a port, the configuration is accepted and the MAC-addresses increased. If you do the opposite and tries to decrease the number of MAC-addresses allowed the command is rejected if it's already learned more addresses then you are trying to configure.
-Port Security: This feature has compatibility issues with other switch features. However Port Security is supported for most features, but these are the ones which is not compatible with Port Security:
*DTP-port (any port running DTP or configured through DTP such as a dynamic access port or a dynamic trunk port)
*Dynamic-access port (any port configured with the command switchport mode dynamic ... DTP)
*SPAN Destination port (you cant send SPAN traffic into a protected port obviously)
*EtherChannel (it's not recommended with etherchannel but it's supported for interfaces up to 100mbit/s)
*Private VLAN:s (in new switches you cant enable PVLANs and Port Security even though technically some features support it)
-There is a feature that can be configured if you want to limit control protocol type of packets simular to the Storm Control feature. It detects if a threshold for the specific protocol is reached and if it is it drops the traffic until it's below the threshold.
This feature - Protocol Storm Protection - is used to limit control protocols such as ARP, ARP snooping, Dynamic Host Configuration Protocol (DHCP) v4, DHCP snooping, Internet Group Management Protocol (IGMP), and IGMP snooping.
Time required: 1 hour & 15 minutes.
Administering the Switch (MAC-address table static entries and aging, NTP, DNS) - Read through Configuration and technology explanations of Administering the switch (MAC-address table static entries and aging).
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swadmin.html#71396
Learned:
-NTP only uses 1 packet per minute to synchronize time. It's extremely effecient!
-NTP selects which time source to used based on the lowest "stratum number". Where number 1 is the source of the time/clock. Or stratum 1 is the location where the actual clock is directly attached to the NTP-server.
-Even if the NTP receiver receives a time from a lower Stratum device it may not synchronize that time. NTP is intelligent enough to compare the time received from multiple devices and if the lower Stratum device time "significally differs from the other NTP sources" it's not going to be used.
-NTP Can be statically configured (ntp server x.x.x.x) in which case there is a two-way communication. Or it can be configured for broadcast, in which case it's only a one-way communication.
-It's possible to disable NTP on VLAN interfaces and routed ports, but not on Access-ports.
-Stack problem: Manually configuring the time and date on a stacked-switch master means that if the stack-master switch fails you have to re-configure this on the new stack-master as it's not synchronized!
-Hostname: As easy as this seems it has to be compliant with the ARPANET standard which implies......They must start with a letter, end with a letter or digit, and have as interior characters only letters, digits, and hyphens. Names can be up to 63 characters
-DNS: If the global domain is configured, example cisco.com, and you configure a hostname of SW1 and tries to ping SW1....the switch will automatically add .cisco.com to that hostname. If the hostname for instance is SW1.cisco.com the switch will not add the default domain-name to the looup process.
In other words, configure the default domain name inside your network and make sure that your DNS-servers handle this domain otherwise the switch will fail to do pings and other things since it will automatically add .configured domain to the hostname when attempting to use protocols such as ping, tftp etc.
-Banners are restricted to 255 characters length.
-MAC table: The default mode is "store-and-forward" which means it will store a complete frame and run a checksum on it before it's forwarded.
-MAC table: As would be expected all MAC-addresses belong to a specific VLAN. However a MAC-address can exist in multiple VLAN:s. But how?
In a well designed network this is unlikely to happen, but it's possible that you use a design with VLAN breakout-switches so that you have a distribution switch where all your VLAN:s are assigned. You then connect VLAN-breakout switches to the distribution switch so that the breakoutswitch is a member of that VLAN of which the distribution switch is configured for.
From the breakout-switch perspective it will be in VLAN1, from the distribution switch perspective it will be in whichever VLAN that the breakout-port is configured to be in.
This is more common in provider networks then in a LAN-environment.
-If you are running a NMS-server (Network Management Server) in your network and you want to track MAC-addresses that ages out and are learned on your switchport it can be cumbersome and impact network performance if there are a lot of changes (guest networks?) . To reduce the SNMP-impact from these traps adjust the SNMP "mac address-table notification change [ interval value ] [ history-size value ]" so that all these traps are grouped in a single Trap rather than multiple traps.
This makes it so that the SNMP-trap that is generated, based on the configured interval, polls the information from the switch activity logs instead and then group it in a single trap!
-It's possible to configure SNMP-traps to be generated when a MAC-address moves inside your network. For example from VLAN 10 to VLAN 20 or if it moves from port fa0/19 to fa0/23.
-A better approach is to configure a SNMP-trap to be genereated if a threshold value is exceeded. Such as the port has used 50% of the available MAC-addresses to be learned.
-Static MAC: Caution! A static MAC-address can result in packets arriving at a port with no static MAC-address assignment to trigger the MAC-flooding out all the ports. Except it's NOT learned because it needs to be statically configured on both ends!
-Static MAC: Easy to misunderstand! When you configure a static MAC-address entry you are telling the switch to make a static decision about where a received Destination MAC-address should be forwarded out. But you also have to specify for which VLAN this static entry should match for!
In other words, be careful. Because the switch will forward received frames based on their Destination MAC-address in the configured Received from VLAN according to your static configuration!
But since you also need to specify which VLAN it was received from and which interface to forward it out! You are basically required to think in revers....
which vlan do i receive traffic on?
Which destination mac address received in that vlan do i want to forward out which interface?
-IT's possible to disable the dynic learning of MAC-addresses on a per VLAN-level. Be extremely cautious when doing this since if it's in a VLAN where you have a SVI-configured for that VLAN - that SVI will flood *all traffic inside that VLAN since there are no MAC-tables to base decisions on*
-As expected you can't disable MAC-address learning on an interface which is configured for RSPAN.
-You can enter the command to disable MAC-address learning on a port currently configured with port-security. However the command is accepted, but the configuration is not effective until you also disable port-security on that port. In other words - it's still learning MAC-addresses if it's a secure port!
Time required: 1½ hour. - Watched INE CCIE Videos about INE covers the L2 Security part before moving on to L3 in their workbook. However the videos cover routing before Security. So the Security part is the last videos in the INE-series. All INE Security videos are in the last part. This specific video: ccie-rsv5-atc-140-high.
Time required: 30 minutes. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-Storm Control page 186.
-MAC-Address Table Static Entries and Aging page 188.
Learned:
-Normally MAC-addresses are populated and learned dynamically so when configured manually they don't age out. This can be used simular to the "blackhole routing to null interface". Just create a static MAC-table entry that points towards an interface that is not in use and all traffic is silently droped because it points to an interface that's not in use.
Note to self: There isn't much to Storm Control and I won't have to re-do that lab before the Lab exam. However I need to pay attention to what the task says, if the task says to assign Storm Control using a relative percentage of the interface bandwidth it just means to check the interface bandwidth and set the level.
The MAC-Address Table Static Entries is more difficult. But i don't need to re-do that lab before the Lab Exam. I feel confident that if I'm given a task to configure static MAC-entries i will solve it. I just have to look out for the words used for the task!
If given an assignment that static entries would solve, just check the interface with the command "show int fa0/x" to get the BIA so you can do the MAC-address table entry. I have to remember to use the BIA-address on the switch that requires the MAC-routing.
Time required: 30 minutes.
 Configuring SPAN and RSPAN
Configuring SPAN and RSPAN
Layer 2
Technology: Configuring SPAN and RSPAN
Learned:
-It's possible to configure the SPAN-destination port to access ingress traffic and assign that traffic to a desired VLAN. Use the command "monitor session 1 destination int fa0/x ingress vlan x" to do that.
-It was odd that the RSPAN required the "monitor session 1 source remote-vlan xxx" command to work even when the VLAN is active and local on the switch. I didn't test it, but the command "monitor session 1 source vlan xxx" should probably achieve the same result. (??)
Note to self: Very straightforward configuration, don't need to re-do these labs. However i got stuck on the RSPAN-vlan for a while and forgot the "remote-span" keyword under the VLAN-config. Very easy to miss and i will have to try and remember that!
Time required: 45 minutes.
Technology: Configuring SPAN and RSPAN
- Read through Configuration and technology explanations of Configuring SPAN and RSPAN.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swspan.html
Learned:
-Only traffic that enter or leaves source ports or source VLANs can be monitored. For example traffic routed towards a source VLAN can not be monitored. The end destination is the SVI so it doesn't enter or leave that VLAN so it can't be monitored.
-With RSPAN you can send monitor traffic towards a destination port where you have a security device, e.g IDS appliance, which then monitors the traffic and can inject and react properly. E.g send TCP reset to a suspicious attacker to close the TCP sessions.
-RSPAN requires the use of a special RSPAN VLAN where all traffic is sent towards the Destination port.
-RSPAN monitors source ports or VLANs and mirrors the traffic towards the destination port/s over the RSPAN VLAN ID. However the original VLAN ID is striped off before, so the network analyzer connected at the destination port can monitor traffic from all VLAN:s without control specific traffic.
-Don't oversubscribe destination ports. Meaning don't source a 100Mbps port to a 10Mbps destination port. Since it's a mirroring technique traffic will be droped for the RSPAN destination port.
-RSPAN requires that the destination port is a remote switchport and not a local switchport. A stacked switch is member of the stack, and all switchports in the stack is considered local regardless of their physical placement.
-SPAN works simular to routing and the traffic monitored or replicated/mirrored depends on if it's RX (inbound) or TX (outbound).
....Inbound traffic is mirrored BEFORE any switch modifications such as QoS.
....Outbound traffic is mirrored AFTER any switch modifications such as QoS.
-It's possible to monitor all type of traffics without anything stripped with the command "encapsulation replicate".
-It's possible that the Destination port receive multiple copies of the same traffic due to the nature of how the mirroring works. For example monitoring port A and B and port A sends traffic towards port B it will be monitored outbound on port A and inbound on port B. Unless it's an IP-packet where TTL and other values change the same traffic is sent twice to the destination port.
-VLAN filtering terminology used with SPAN has nothing to do with VACLs or PACLs, but it limits which VLAN:s can be monitored and is allowed to pass a trunk-port when SPAN is configured. The vlan-filter option with SPAN configures which VLANs are allowed on the trunk, not which are being filtered !!
-RSPAN configuration can be propagated by VTP for VLAN range 1-1005. For extended VLAN-range VTP version 3 is required.
-If a physical port is monitored that is part of an EtherChannel only the traffic that uses that physical port is monitored.
-It's possible to create an ACL to capture interesting traffic that should be mirrored by the SPAN session.
-If your hardware memory resources are low security ACL's will be treated with higher priority than the SPAN ACL's. As in the SPAN ACL's will be "unloaded" until more memory is available.
Time required: 2 hours. - I have not found any INE videos that are covering SPAN and RSPAN, so i will have to look for other video sources here, or just skip videos for this part it's fairly straightforward. It's a very small topic in the blueprint so i will take a guess that the theory will be enough for the Lab!
Time required: 0 minutes. - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-SPAN page 192.
-RSPAN page 194.
Learned:
-It's possible to configure the SPAN-destination port to access ingress traffic and assign that traffic to a desired VLAN. Use the command "monitor session 1 destination int fa0/x ingress vlan x" to do that.
-It was odd that the RSPAN required the "monitor session 1 source remote-vlan xxx" command to work even when the VLAN is active and local on the switch. I didn't test it, but the command "monitor session 1 source vlan xxx" should probably achieve the same result. (??)
Note to self: Very straightforward configuration, don't need to re-do these labs. However i got stuck on the RSPAN-vlan for a while and forgot the "remote-span" keyword under the VLAN-config. Very easy to miss and i will have to try and remember that!
Time required: 45 minutes.
 Configuring Voice VLANs
Configuring Voice VLANs
Layer 2
Technology: Configuring Voice VLANs
Learned:
-There are basically three options to configure a switchport to support VOICE/IP Phones.
1. Configure the switchport as a trunk-port and have the phone send the voice-traffic tagged for the voice vlan. The phone will send the pc/data traffic as untagged to the trunk-port so here you would have to configure the trunk's native VLAN to be whatever the data-VLAN should be. (because data traffic is sent untagged the trunk-port should put these untagged data frames in the data vlan....hence set up the native-vlan on this trunk to be the same as the Data-vlan)
2. Worst possible implementation is to just run the Voice and the Data traffic in a single VLAN so that the phone acts as a simple bridge. In this scenario the only thing that needs to be configured is the "switchport mode access, switchport access vlan x" to make this work.
3. Use a single VLAN for both the Voice and Data traffic but add 802.1p priority to the frames so that the phone sends the data and voice traffic as 802.1Q frame with VLAN ID 0 with 802.1p CoS values. The switch will treat these 802.1Q frames as members of the access-vlan but it will also read the priority values for QoS so at least you get some traffic-classification with this.
-When using the command "switchport voice vlan x" the port will be "automatically a trunk" with the native vlan configured to that of the access-vlan and it will enable PortFast.
Note to self: Very simple lab and I don't have to re-do this. I just have to look out for weird/odd ways of assigning tasks. Such as "allow only vlan x and y" on the voice port (which basically means add the command "switchport trunk allowed vlan x,y" even if it's not a trunk-port).
Also look out for if the task says to "assign voice vlan x through CDP" it just means to configure the voice vlan with the command "switchport voice vlan x" since that's what CDP will use as it's Voice VLAN. There is no CDP-command that specifically tells this!
Time required: 15 minutes.
Technology: Configuring Voice VLANs
- 1Read through Configuration and technology explanations of Configuring Voice VLANs.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swvoip.html
Learned:
-The built-in 3-port switch on a Cisco IP-phone passes through traffic in "untrusted" mode by default. Meaning that every data-traffic that passes through the phone-switch is marked with a CoS (Class of Service) value of 0.
Time required: 15 minutes - I have not found any INE videos that are covering Voice VLANS, so i will have to look for other video sources here, or just skip videos for this part it's fairly straightforward. It's a very small topic in the blueprint so i will take a guess that the theory will be enough for the Lab!
- Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-Voice VLAN page 197.
Learned:
-There are basically three options to configure a switchport to support VOICE/IP Phones.
1. Configure the switchport as a trunk-port and have the phone send the voice-traffic tagged for the voice vlan. The phone will send the pc/data traffic as untagged to the trunk-port so here you would have to configure the trunk's native VLAN to be whatever the data-VLAN should be. (because data traffic is sent untagged the trunk-port should put these untagged data frames in the data vlan....hence set up the native-vlan on this trunk to be the same as the Data-vlan)
2. Worst possible implementation is to just run the Voice and the Data traffic in a single VLAN so that the phone acts as a simple bridge. In this scenario the only thing that needs to be configured is the "switchport mode access, switchport access vlan x" to make this work.
3. Use a single VLAN for both the Voice and Data traffic but add 802.1p priority to the frames so that the phone sends the data and voice traffic as 802.1Q frame with VLAN ID 0 with 802.1p CoS values. The switch will treat these 802.1Q frames as members of the access-vlan but it will also read the priority values for QoS so at least you get some traffic-classification with this.
-When using the command "switchport voice vlan x" the port will be "automatically a trunk" with the native vlan configured to that of the access-vlan and it will enable PortFast.
Note to self: Very simple lab and I don't have to re-do this. I just have to look out for weird/odd ways of assigning tasks. Such as "allow only vlan x and y" on the voice port (which basically means add the command "switchport trunk allowed vlan x,y" even if it's not a trunk-port).
Also look out for if the task says to "assign voice vlan x through CDP" it just means to configure the voice vlan with the command "switchport voice vlan x" since that's what CDP will use as it's Voice VLAN. There is no CDP-command that specifically tells this!
Time required: 15 minutes.
 Configuring Private VLANs
Configuring Private VLANs
Layer 2
Technology: Configuring Private VLANs
Learned:
-Protected Ports is a mini-version of the Private VLANs. Essentially blocking switchports in the same VLAN from communicating with each other. This doesn't span multiple switches so if hosts are in two different switches and you configure protected ports, they will be able to talk with each other as long as they cross the trunk-port. However the local traffic within the switch will be blocked.
-Private VLANs can be propagated by VTP version 3, otherwise it requires VTP Transparent mode to work.
-The terminology used with PVLANs are very difficult to configure since it's easy to mix them up. But here's the best way to configure them:
The key here to remember is the order, and the CLI ? will not help you at all!
Note to self: I feel extremely confident with the theory behind PVLANs and how they work. I also feel very confident in configuring them, i shouldn't need to re-do this lab. If i get a PVLAn assignment task on the Lab-exam i will just look at the configuration guide for PVLANs since they're available during the exam. It's just too risky to mix this up so it's better to just follow the guide!
Time required: 30 minutes.
Technology: Configuring Private VLANs
- Read through Configuration and technology explanations of Configuring Private VLANs.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swpvlan.html
Learned:
-Easier explained Private VLANs are subdomains of the topdomain. The topdomain is the Primary VLAN and the subdomains are the Secondary VLANs. All secondary VLANs are members of the topdomain - the Primary VLAN.
-Technically this is how the different ports work:
*Promiscuous - Sends and Receives traffic to all Secondary VLANs.
*Isolated - Sends traffic only to the Promiscuous port and receives traffic only from the Promiscuous port.
*Community - Sends traffic to ports in the same community and towards the Promiscuous port. Receives traffic from ports in the same Community and from the Promiscuous port.
-If the promiscuous port in a stacked-switch configuration fails, all the private VLAN:s are isolated from communicating outside the primary VLAN.
-Only one instance of STP runs on the primary VLAN even if you configure multiple Secondary VLANs as part of the primary VLAN. STP copies the configuration for the Primary VLAN down to the Secondary VLANs.
-VLAN Maps should be applied at both the Primary and the Secondary VLANs to filter out specific IP-traffic.
-Private VLANs is a Layer 2 security feature and doesn't stop hosts from communicating at Layer 3 (obviously!)
-Private VLANs is not compatible with the following features:
*dynamic-access port VLAN membership,
*Dynamic Trunking Protocol (DTP), Port Aggregation Protocol (PAgP),
*Link Aggregation Control Protocol (LACP),
*Multicast VLAN Registration (MVR),
*Voice VLAN,
*Web Cache Communication Protocol (WCCP)
Time required: 30 minutes. - Watched the INE CCIE Videos about Private VLANs.
Time required: 30 minutes - Did the following labs (Advanced Technology Labs) from the INE RSv5 workbook:
-Protected Ports page 183. (not technically PVLANs but mini-PVLANs so i grouped them)
-Smartport Macros page 201. (not technically PVLANs but it doesn't fit anywhere)
-Private VLANs page 206.
Learned:
-Protected Ports is a mini-version of the Private VLANs. Essentially blocking switchports in the same VLAN from communicating with each other. This doesn't span multiple switches so if hosts are in two different switches and you configure protected ports, they will be able to talk with each other as long as they cross the trunk-port. However the local traffic within the switch will be blocked.
-Private VLANs can be propagated by VTP version 3, otherwise it requires VTP Transparent mode to work.
-The terminology used with PVLANs are very difficult to configure since it's easy to mix them up. But here's the best way to configure them:
- Create the primary VLAN and assign it as a private-vlan primary.
- Create the secondary VLANs and assign them as either isolated or community.
- Go back to the primary VLAN and associate the secondary-vlans to the primary vlan.
- Go to your host-ports and configure them as "switchport mode private-vlan host" followed byt the command "switchport private-vlan host-association Primary_VLAN Secondary_VLAN.
- Go to the promiscuous port and configure it with "switchport private-vlan promiscuous" or if you are using SVI for Inter-VLAN routing use the command "private-vlan mapping secondary VLANs."
The key here to remember is the order, and the CLI ? will not help you at all!
Note to self: I feel extremely confident with the theory behind PVLANs and how they work. I also feel very confident in configuring them, i shouldn't need to re-do this lab. If i get a PVLAn assignment task on the Lab-exam i will just look at the configuration guide for PVLANs since they're available during the exam. It's just too risky to mix this up so it's better to just follow the guide!
Time required: 30 minutes.
 Configuring Miscellaneous Features (CDP , LLDP, ERSPAN)
Configuring Miscellaneous Features (CDP , LLDP, ERSPAN)
Layer 2
Technology: Configuring Miscellaneous Features (CDP , LLDP, ERSPAN)
Note to self: I feel confident with both CDP and LLDP and less confident with ERSPAN mainly because you would need access to a 6500 switch to even mess with the configuration. I will re-study the ERSPAN theory before the Lab-exam because I don't think they will implement it on their switching-domain since it's not based on 6500-switches and they officially said that there won't be any platform-specific configuration tasks. ERSPAN is most certainly platform specific!
Technology: Configuring Miscellaneous Features (CDP , LLDP, ERSPAN)
- Read through Configuration and technology explanations of Configuring CDP.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swcdp.html
Learned:
-Not exactly learned anything but worth writing down. Since it's a layer 2 protocol it means that it will discover neighbors and save information about neighbors regardlass of which higher level protocol the devices runs. In other words you can run different Network layer protocols or Transport layer protocols and CDP will still work.
-CDP like many protocol have various timers that can be tuned to increase effeciency of CDP.
Time required: 5 minutes tops. - Read through Configuration and technology explanations of Configuring LLDP.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_1_se/configuration/guide/3750xcg/swlldp.html
Learned:
-LLDP is a non-cisco proprietary version of CDP that achieves the same function. Although LLDP comes with a few additional configuration parameters called "Type, Length, Value" or simply TLVs.
-LLDP-MED is an extention to the LLDP protocol used to support Media Endpoint Devices. For example IP-phones. To do that additional TLVs are used that can control which Voice VLAN to use for the IP-Phones, how their QoS priorities should be configured, How much Power they should use if they're PoE enabled and so on.
-LLDP does not work on tunneling ports.
-You can configure network-policy profiles for LLDP and when applied you can't configure a Voice vlan with the command "switchport voice vlan x" if the LLDP network policy is configured first. However if the voice-vlan is configured first the network-policy TLV uses that voice VLAN.
-As with CDP it's possible to configure a lot of parameters manually. For example how often to send or receive information, which TLV's to send or receive and so on.
-LLDP sends only LLDP-packets until it receives LLDP-MED TLV's. If it stops receiving LLDP-MED TLV's the port reverts back to sending only LLDP-packets. These TLV's can be manually enabled or disabled in interface configuration mode.
Time required: 15 minutes. - Read through Configuration and technology explanations of Configuring ERSPAN.
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/span.html#wp1020356
Note: It's very weird that cisco says that they will not test you on platform-specific topics and yet they include ERSPAN which only works on the Catalyst 6500 switch or Nexus platforms or the IOS-XE versions. There is not ERSPAN for the 15.0 Catalyst 3560X and 3750X, so the only place to look is from the 6500 configuration guide on ios 12.2SX.
Learned:
-ERSPAN uses a GRE tunnel to carry the mirrored traffic. This means that ERSPAN is specifically used to monitor remote networks where you need to transport the data across an IP-network using for example GRE.
With this it's possible to setup a SPAN-session that collects data from different regions, countries or sites and collaborate them across an IP-network. So you wouldn't need to be in the same Layer 2 domain as you need with RSPAN.
-ERSPAN source sessions do not copy local RSPAN VLAN source traffic or locally sourced ERSPAN GRE traffic.
-ERSPAN explained easier is simply RSPAN over an IP-network.
-For ERSPAN to be supported on the Catalyst 6500 platform a 720 Supervisor Engine is required - otherwise it's not supported. (another odd reason why cisco has this in the blueprint).
-ERSPAN adds a 50-byte header to the copies Layer 2 frame and replaces the 4-byte CRC trailer.
-ERSPAN supports Jumbo-frames up to 9202 bytes.
-ERSPAN ignores the configured MTU values and will create Jumbo-frames up to 9202 bytes. So if any interface along the forwarding path enforces lower MTUs than 9202 the ERSPAN traffic can be dropped.
This also means that if an interface enforces the default 1500byte MTU (payload) remember that ERSPAN requires an additional 50 byte so any payload longer than 1450 bytes will be droped. 1450 bytes for standard frames, + 50 bytes for ERSPAN header, + 18 byte for Ethernet header = 1518 bytes.
Time required: 45 minutes. - I have not found any INE videos that are covering ERSPAN, so i will have to look for other video sources here, or just skip videos for this part. The way i reason here is that ERSPAN is a platform specific topic, and even though it's in the blueprint it will - and can only - work on the Catalyst 6500 switch with a supervisor engine.
Cisco is using IOL/IOU in the lab based on the 3560X and 3750X platforms so unless they are doing something funky it will not be an issue, it will most likely show up on the Diagnostics section because there won't be any 6500-switches in the lab.
Note to self: I feel confident with both CDP and LLDP and less confident with ERSPAN mainly because you would need access to a 6500 switch to even mess with the configuration. I will re-study the ERSPAN theory before the Lab-exam because I don't think they will implement it on their switching-domain since it's not based on 6500-switches and they officially said that there won't be any platform-specific configuration tasks. ERSPAN is most certainly platform specific!
 Configuring Multi PPP Ethernet, PPP & HDLC
Configuring Multi PPP Ethernet, PPP & HDLC
Layer 2
Technology: Configuring Multi PPP Ethernet, PPP & HDLC
Note to self: I kept my studying to HDLC and PPP that I believe to be in the scope of the CCIE RSv5 Blueprint by cisco. ISDN-stuff is not there, Frame-relay is not there. So it makes no sense to study those topics!
Note to self 2: I know myself to be very weak in PPP and serial interfaces in general. Mainly because there is not a single serial interface within about 1500 miles radius from my location. It's an extremely old, low bandwidth interface that I know i will not come in touch with.
In other words I need to study this and pay more attention, specifically PPP with LCP-states. I know CHAP and PAP, but not the "expert depth and details" about Serial communication and PPP.
In case someone is Reading this, my situation is that for the last 10 years all our Connections in Sweden are using Ethernet. ISP's don't even sell ISDN or Frame-Relay type of Connections anymore and haven't for over 10 years! There are just a few of these legacy Connections around, except for FR which is completely gone, and all ISP's are doing what they can to get rid of them.
Don't mistake this for ATM-lines like DSL-Connections. But the end-customer (whoever buys something from the ISP, private or Commercial) will Always get an Ethernet-end to plug into!
HDLC,PPP and PPPoE is definatly type of topics that any modern or decent-modern network will never see or use. PPPoE is a different matter, but serial Connection is considered legacy and they did get rid of FR why not the serial lines as well ? *shrugs*
Time required: 45 minutes.
Technology: Configuring Multi PPP Ethernet, PPP & HDLC
- Read through Configuration and technology explanations of Configuring Multi PPP Ethernet and PPP.
http://www.cisco.com/c/en/us/td/docs/ios/dial/configuration/guide/12_4/dia_12_4_book/dia_media-ind_multi_ppp.html
Learned:
-"ppp authentication chap", should only be used with TACACS.
-Software Compression can be configured for PPP, in which case the same compression method must be used at both sides of the link.
-Compression is CPU-intensive so watch out that the CPU usage is not over 65% with "show process cpu" when compression is enabled.
-Compressed files (such as RAR, ZIP etc) does not benefit from PPP compression. Only uncrompressed data benefits from it and can be compressed.
-It's possible to configure a PPP-interface as a DHCP-proxy for clients that Dial into the interface. The PPP interface then acts as an agent between the DHCP-server and the clients of the PPP interface.
-When using PPP and CHAP the default "discriminator" is to use the hostname. This can be re-configured with the command "ppp chap hostname" or "ppp pap sent-username".
-It's possible to enable Interleaving of smaller packets when using Multilink PPP (MLP). When configured that interface will try to "squeeze" in smaller packets between larger fragmented packets. The implementation problem it tries to solve is for Real-time sensitive traffic such as VoIP.
-PPP authentication does not mean that both sides will be configured for authentication. PPP authentication is a "challange & response" protocol. Meaning that when you configure "ppp authentication pap" you tell that specific interface/router to challenge the other side.
The other side must then send a challenge-response that the challange-request side accepts. This is not a two-way communication in such way that you can challenge in One direction but not the other!
-By default when using PPP CHAP the response challenge will use it's hostname by default as the username. So to specify which username to send by default as the challenge-response, use the command "ppp chap hostname abcdefg".
-CHAP requires passwords to be stored in clear-text, otherwise the challenge-request router will not be able to perform the MD5-hash correctly. It will "hash a hashed password" instead of "creating a hash from a stored password". Authentication will fail in this case!
Time required: 1 hour 15 minutes. - Read through Configuration and technology explanations of Configuring HDLC.
There is absolutely no good documentation about HDLC on ciscos website and what is to be found is horrible compared to other places.
There is very little about HDLC and since its a proprietary protocol it makes sense to assume that you need to know how to enable HDLC and configure compression. Since HDLC requires a serial-interface (legacy port IMO) I had to dig up the configuration guide for a router instead of a switch. I choose the 819 configuration guide because it had what i was looking for about HDLC configuration.
http://www.cisco.com/c/en/us/td/docs/routers/access/800/819/software/configuration/Guide/819_SCG/6ser_conf.html
For a much more in depth-explanation of how HDLC works I also read this, which explains it more thoroughly. I didn't spent too much time looking at this though since this is the HDLC-standard and not the Cisco version of HDLC.
http://www.erg.abdn.ac.uk/users/gorry/eg3561/dl-pages/hdlc.html
Learned:
-Ciscos version of HDLC is proprietary and should be refered to as cHDLC as it's not a standard. Cisco adds additional information to the HDLC frame-header for a "control protocol", for example the SLARP (Serial Line Address Resolution Protocol).
-SLARP is a cisco addition to HDLC that tries to configure ip-addresses on a Point-to-Point link. It does that by knowing that a Point-to-Point link is exactly two hosts. So if the other end of the serial-interface has an ip-address configured I can safely take the other available address to use on my side. That's how it works.
-The encapsulation configuraton on the physical interface is inherited to all sub-interfaces if the physical interface encapsulation is changed. And all the configuration for the sub interfaces are still in use.
-HDLC can be configured for compression which uses algorithm Stacker LZS.
-HDLC requires a clockrate to be configured for L1. One end is the DCE side, the other end is the DTE side. The DCE-side should send the clock-rate on the link, if the DTE-side receives this clock rate the link will be Up/Up since there is no Layer 2 addresses required for a HDLC-link to become up/up. All it requires is a synchronization between the DCE and the DTE-side.
Time required: 30 minutes. - Watched the INE CCIE Videos about HDLC and PPP.
Time required: 1 hour. - There are no PPP or HDLC labs in the INE CCIE RSv5 workbook. In this perticular case I will just use GNS3 and setup simple PPP for serial interfaces and then do PPPoE in the same time.
Learned:
-Learned to use "debug ppp negotiations" and "debug ppp authentication" to see how a PPP connection is formed over LCP.
-Learned that PPP PAP or CHAP is a challenge protocol meaning that you only need "ppp authentication chap/pap" in one end of the connection and then setup the response-side with the correct passwords.
-The LCP (Link Control Protocol) that is used with PPP is becoming open only after authentication works. If configured to do so, which is is by default, it will then install the IPCP (IP Control Protocol) which will find out what the other end of the line is using as an ip-address and assign the other available host address to it's interface. It will also install a Host-route (255.255.255.255/32) with that ip-address.
This is legacy behaviour when back in the time it was more common to assign ip-addresses of a pool that was not local to the subnet that was being dialed-into. In that case this host route-got redistributed into the IGP so that traffic could be forwarded towards the host that dialed-in.
Note to self: I kept my studying to HDLC and PPP that I believe to be in the scope of the CCIE RSv5 Blueprint by cisco. ISDN-stuff is not there, Frame-relay is not there. So it makes no sense to study those topics!
Note to self 2: I know myself to be very weak in PPP and serial interfaces in general. Mainly because there is not a single serial interface within about 1500 miles radius from my location. It's an extremely old, low bandwidth interface that I know i will not come in touch with.
In other words I need to study this and pay more attention, specifically PPP with LCP-states. I know CHAP and PAP, but not the "expert depth and details" about Serial communication and PPP.
In case someone is Reading this, my situation is that for the last 10 years all our Connections in Sweden are using Ethernet. ISP's don't even sell ISDN or Frame-Relay type of Connections anymore and haven't for over 10 years! There are just a few of these legacy Connections around, except for FR which is completely gone, and all ISP's are doing what they can to get rid of them.
Don't mistake this for ATM-lines like DSL-Connections. But the end-customer (whoever buys something from the ISP, private or Commercial) will Always get an Ethernet-end to plug into!
HDLC,PPP and PPPoE is definatly type of topics that any modern or decent-modern network will never see or use. PPPoE is a different matter, but serial Connection is considered legacy and they did get rid of FR why not the serial lines as well ? *shrugs*
Time required: 45 minutes.
 Configuring and understanding PPPoE
Configuring and understanding PPPoE
Layer 2
Technology: Configuring and understanding PPPoE

The goal was to just try out the features of PPP and PPPoE over both Serial interfaces and Ethernet-interfaces. My end goal with this lab i just created here was to run PPP over the serial lines between R2 and R3 and over the Ethernet connection between R1 and R2. This would require a PPPoE session between R2 and R1.
I'll just use 10.0.0.1/30 on R2 and 10.0.0.2/30 on R3 on the serial.
I'll use 192.168.0.10 on R1 and 192.168.0.20 on R2 on the ethernet-link.
Note: Since im using IOL/IUO for some smaller labs i run into a lot of issues with simple stuff like ARP. In this perticular case i had to setup a middle-switch and flap the interfaces for this to work but it's not required. IOL/IUO is extremely unstable but requires almost no resources! So beware!
So Step 1: Just ping between the Point-to-Point links (R1-R2, R2-R3) to verify basic IP connectivity over Ethernet and HDLC.
Step 2: Setup R2 as the PPPoE session server betwen R1 and R2.
Not as easy as one would think. The documentation from the cisco-webpage was out of date. According to documentation here is how you setup the server:
......the broadband aggregation protocol setup.....
configure terminal
bbba-group pppoe R1
virtual-template 1
end
......link the physical interface to the bba-group.....
configure terminal
interface ethernet 0/0
pppoe enable group R1
end
That looks OK to me but that doesn't work because there's one step missing...
......configure the virtual-template interface......
configure terminal
interface virtual-template 1
ip address 192.168.0.20 255.255.255.0
Step 3: Setup R1 as the PPPoE client to use PPP with R2.
Simple enough, all we have to do is configure the dial interface (since we're dialing in to the PPPoE server), configure the dial-interface with an ip-address and link the dial-pool to the physical interface.
.....configure dial interface.....
interface Dialer1
mtu 1492
ip address 192.168.0.10 255.255.255.0
encapsulation ppp
dialer pool 1
! dialer-group command not needed for this to work but it's in the cisco documentation
dialer-group 1
end
....link the dial-interface to the physical interface....
interface Ethernet0/0
no ip address
pppoe enable
pppoe-client dial-pool-number 1
pppoe-client ppp-max-payload 1492
end
Step 4. Test connectivity between R1 and R2. Notice that since this is a dial-up connection some new interfaces will be showing up that is only visible when using dial-up connections.
First have a look at R1:
There is the Dialer1 interface we created and configured with an ip-address, but there's also a Virtual-Access1 interface in the Up/Up state.
Second let's look at R2:

Here's again the virtual-Template1 interface configured with our ip-address. But also note that the Virtual-Access1.1 interface is also using this ip-address. And that the Virtual-Template interface is in down/down while the Virtual-Access1.1 interface is in the Up/Up state.
This means that we should be able to ping 192.168.0.10 and 192.168.0.20, right? Let's try:

Fair enough, it works between R1 to R2. So let's have a look at what happens over at R2.
Remember that we're dialing into R2, and that we are using PPP so there should be a local route to R1 in the routing table.
Let's check at R2:

Sure enough there is a connected route to 192.168.0.10/32 over the Virtual-Access1.1 interface.
Now let's see if we can ping from R2:

Not the expected results. We can reach R1 but we can't ping the local Virtual-Template interface of R2.
Here we would normally troubleshoot by checking the arp-table, but it should be empty. Since we are encapsulation Ethernet over PPP we are not using Ethernet so there's no need for arp! Let's double check:


As expected the ARP-cache is emtpy since we are using PPP. But notice that the "show pppoe session" command displays information about the dial-session between R1 and R2.
But to solve the problem of R2 not being able to ping the 192.168.0.20 address we would have to do some debugging and figure out why. So I just enabled "debug ip packet detail" on R2 and tried to ping 192.168.0.20.
Looking at this debug output I can see that the router tried to route it through the FIB where it knows about 192.168.0.20/32, we can verify it with "show ip cef":

As we can see we have a FIB-entry for 192.168.0.20/32 on interface Virtual-Access1.1.
This means that the router would need to forward it to it's own route-processor. However that has nothing to do with our issue here.
This is just how the PPPoE server interfaces work.
There is a workaround which is to setup a loopback-interface and assign this address to the virtual-template it will solve the problem:

Much better for general troubleshooting issues. Now we can ping everywhere even locally .
.
Last thing i want to do is just setup basic IGP between R2 and R3 to verify that we can reach R1 over the PPP serial link and over the PPPoE session.
This requires to setup basic routing, so i just went with RIPv2 between R2 and R3 and a static route between R1 and R2.
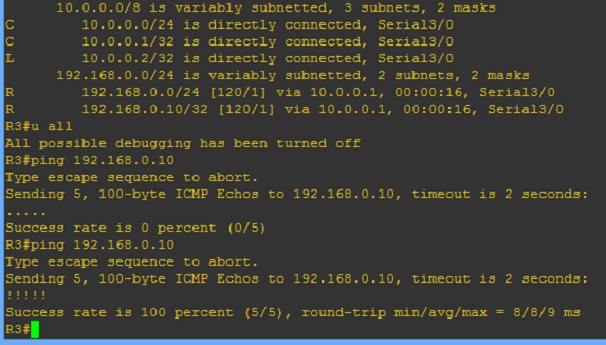
Perfect. After a bit of messing around I'm happy with the outcome.
Note to self: I feel confident with all the topics that they could throw at me in terms of PPP and PPPoE.
The only problem is, i lack all sorts of experience with PPP since it's not used around my regions.
I should have to remember the lab I created her and study it before the Lab-exam just to make sure I remember the order of configuration. PPP, PAP, CHAP shouldn not be a problem.
I will also need to remember how to find the configuration-examples for PPPoE server / client through the cisco-website since it's available during the exam and PPPoE is a topic which is better used with configuration guides.
Time required: 1½ hour.
Technology: Configuring and understanding PPPoE
- Read through Configuration and technology explanations of Providing Protocol Support for Broadband Access Aggregation of PPPoE sessions.
Note: This section covers a lot of ISP-related stuff that are not in the CCIE RSv5 blueprint. However it explains really good what you can achieve with PPPoE and how you setup a PPPoE server (which is needed for the labs). It's not required to read all of this, all you need is how to setup the server.
Just learn how to reach this page and go to the configuration examples, in case you should get PPPoE on the lab!
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/bbdsl/configuration/15-mt/bba-15-mt-book/bba-pppoe-baa.html
It's odd but there is no concept explanation for PPPoE in the configuration document. So also read this link to undersand what Broadband Access Aggregation actually is:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/bbdsl/configuration/15-mt/bba-15-mt-book/bba-understanding.html
Learned:
-The terminology Broadband Access Aggregation simply means to setup a network to allow multiple access-mediums to connect through VPN or other means. It's a technique to aggregate multiple access-mediums into one. That's where PPP comes in since it's media-independent!
-PPP is often used to Tunnel other protocols. Tunneled protocol gains additional headers and becomes encapsulated inside the tunneling-protocol, such as L2TP. For example it's possible to encapsulate an IP or TCP or UDP protocol information inside another protocol that transports it over a non IP-network or TCP or UDP-aware network.
-PPPoE sessions in IOS 15.0 uses "profiles" which is different from how you configure them in IOS 12.4. To migrate, upgrade IOS to version 15 and use PPPoE session profiles instead.
-The step to configuring PPPoE server can be summarized into two steps:
....Setup the virtual-template and the bba-group....
enable
configure terminal
bbba-group pppoe NAME
virtual-template 1
end
....Setup the interface to participate in the BBA-group.....
enable
configure terminal
interface fa0/1
pppoe enable group NAME
end
Time required: 30 minutes
This should be the only thing that is part of the CCIE RSv5 Lab exam because all the other stuff with PPPoE is Service-Provider related! - Read through Configuration and technology explanations of PPP over Ethernet Client.
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/bbdsl/configuration/15-mt/bba-15-mt-book/bba-ppoe-client.html
Note: Within the scope of the CCIE RSv5 Blueprint it only says "implement PPPoE, Troubleshoot PPPoE". But since they declared that they build the lab exam based on ISR 2900-series routers and 3750X switches it's safe to assume that you only need to know how to setup an interface to initiate a PPPoE session and not know all the Service-provider related details.
Learned:
-PPPoE Clients are typically used at the edge of a LAN that connects to a DSL-line or other type of network medium. An image better illustrates this:
-PPPoE requires an additional 8 bytes of header information to work properly. Therefor it's usually required to adjust the MTU-values to 1492 because you should not send a payload higher than 1492 when using PPPoE.
-It's possible, but not recommended, to increase the MTU payload size with the command "pppoe-client ppp-max-payload".
-Configuring an Ethernet interface for PPPoE session consist of two steps:
....Configure the Dial-pool....
(This sets up the dial-interface and the pool which we will use for the PPPoE client to initiate the session)
enable
configure terminal
interface dialer 1
mtu 1492
encapsulation ppp
ip address negotiated/configure an address static
dialer pool 1
dialer-group group 1
end
....Configure the Ethernet interface for PPPoE....
(this configures the actual physical interface do use the dial-interface to initiate the PPPoE session)
enable
configure terminal
interface ethernet fa0/1
pppoe-client dial-pool-number 1
pppoe-client ppp-max-payload 1500
end
Time required: 30 minutes. - Watched the INE CCIE Videos about HDLC and PPP.
Time required: 30 minutes. - There are no PPPoE labs in the INE CCIE RSv5 workbook. In this perticular case I will just use GNS3 and setup simple PPP for ethernet interfaces and then do a PPPoE session in the same time.
I used this very simple topology for my lab:

The goal was to just try out the features of PPP and PPPoE over both Serial interfaces and Ethernet-interfaces. My end goal with this lab i just created here was to run PPP over the serial lines between R2 and R3 and over the Ethernet connection between R1 and R2. This would require a PPPoE session between R2 and R1.
I'll just use 10.0.0.1/30 on R2 and 10.0.0.2/30 on R3 on the serial.
I'll use 192.168.0.10 on R1 and 192.168.0.20 on R2 on the ethernet-link.
Note: Since im using IOL/IUO for some smaller labs i run into a lot of issues with simple stuff like ARP. In this perticular case i had to setup a middle-switch and flap the interfaces for this to work but it's not required. IOL/IUO is extremely unstable but requires almost no resources! So beware!
So Step 1: Just ping between the Point-to-Point links (R1-R2, R2-R3) to verify basic IP connectivity over Ethernet and HDLC.
Step 2: Setup R2 as the PPPoE session server betwen R1 and R2.
Not as easy as one would think. The documentation from the cisco-webpage was out of date. According to documentation here is how you setup the server:
......the broadband aggregation protocol setup.....
configure terminal
bbba-group pppoe R1
virtual-template 1
end
......link the physical interface to the bba-group.....
configure terminal
interface ethernet 0/0
pppoe enable group R1
end
That looks OK to me but that doesn't work because there's one step missing...
......configure the virtual-template interface......
configure terminal
interface virtual-template 1
ip address 192.168.0.20 255.255.255.0
Step 3: Setup R1 as the PPPoE client to use PPP with R2.
Simple enough, all we have to do is configure the dial interface (since we're dialing in to the PPPoE server), configure the dial-interface with an ip-address and link the dial-pool to the physical interface.
.....configure dial interface.....
interface Dialer1
mtu 1492
ip address 192.168.0.10 255.255.255.0
encapsulation ppp
dialer pool 1
! dialer-group command not needed for this to work but it's in the cisco documentation
dialer-group 1
end
....link the dial-interface to the physical interface....
interface Ethernet0/0
no ip address
pppoe enable
pppoe-client dial-pool-number 1
pppoe-client ppp-max-payload 1492
end
Step 4. Test connectivity between R1 and R2. Notice that since this is a dial-up connection some new interfaces will be showing up that is only visible when using dial-up connections.
First have a look at R1:

There is the Dialer1 interface we created and configured with an ip-address, but there's also a Virtual-Access1 interface in the Up/Up state.
Second let's look at R2:

Here's again the virtual-Template1 interface configured with our ip-address. But also note that the Virtual-Access1.1 interface is also using this ip-address. And that the Virtual-Template interface is in down/down while the Virtual-Access1.1 interface is in the Up/Up state.
This means that we should be able to ping 192.168.0.10 and 192.168.0.20, right? Let's try:

Fair enough, it works between R1 to R2. So let's have a look at what happens over at R2.
Remember that we're dialing into R2, and that we are using PPP so there should be a local route to R1 in the routing table.
Let's check at R2:

Sure enough there is a connected route to 192.168.0.10/32 over the Virtual-Access1.1 interface.
Now let's see if we can ping from R2:

Not the expected results. We can reach R1 but we can't ping the local Virtual-Template interface of R2.
Here we would normally troubleshoot by checking the arp-table, but it should be empty. Since we are encapsulation Ethernet over PPP we are not using Ethernet so there's no need for arp! Let's double check:


As expected the ARP-cache is emtpy since we are using PPP. But notice that the "show pppoe session" command displays information about the dial-session between R1 and R2.
But to solve the problem of R2 not being able to ping the 192.168.0.20 address we would have to do some debugging and figure out why. So I just enabled "debug ip packet detail" on R2 and tried to ping 192.168.0.20.

Looking at this debug output I can see that the router tried to route it through the FIB where it knows about 192.168.0.20/32, we can verify it with "show ip cef":

As we can see we have a FIB-entry for 192.168.0.20/32 on interface Virtual-Access1.1.
This means that the router would need to forward it to it's own route-processor. However that has nothing to do with our issue here.
This is just how the PPPoE server interfaces work.
There is a workaround which is to setup a loopback-interface and assign this address to the virtual-template it will solve the problem:

Much better for general troubleshooting issues. Now we can ping everywhere even locally
Last thing i want to do is just setup basic IGP between R2 and R3 to verify that we can reach R1 over the PPP serial link and over the PPPoE session.
This requires to setup basic routing, so i just went with RIPv2 between R2 and R3 and a static route between R1 and R2.

Perfect. After a bit of messing around I'm happy with the outcome.
Note to self: I feel confident with all the topics that they could throw at me in terms of PPP and PPPoE.
The only problem is, i lack all sorts of experience with PPP since it's not used around my regions.
I should have to remember the lab I created her and study it before the Lab-exam just to make sure I remember the order of configuration. PPP, PAP, CHAP shouldn not be a problem.
I will also need to remember how to find the configuration-examples for PPPoE server / client through the cisco-website since it's available during the exam and PPPoE is a topic which is better used with configuration guides.
Time required: 1½ hour.
 Final notes about Layer 2 technologies bofore moving on to Layer 3
Final notes about Layer 2 technologies bofore moving on to Layer 3
Layer 2
Technology: None specific, just Writing down some things to consider since Layer 2 studies and notes are now completed.
I did expect it to take a lot longer to go through the layer 2 sections of the Blueprint.
The time i wrote down during my studies of Layer 2 is not a direct representation of how much time i have invested in studying.
There is a lot of time to be added to Layer 2 studies that I've not taken the time to write down.
Here are some pieces that have required a lot of time that is not included in the time-required that i've written down:
-Writing down the study notes per technology.
-Browsing various forums, discussing various networking topics at other forums, Reading books, RFC's and other things.
-Doing research of how to prepare for the CCIE RSv5 including which videos to view, which topics to study, which vendor to work with, which platforms to use, which topology to use.
All-in-all....i wrote down my time required by working through the INE Topology and their CCIE RSv5 Workbook that I'm using.
That was my intention with these study notes so I know how much time i have invested with their Workbook in case i have to re-study something Before the Exam.
I can't estimate the time i've invested doing other things, but for those interested i will say it's an additional 100-150 hours except doing these labs and Reading the configuration guides!
Layer 2 topics saved for last:
....yes there is more to Layer 2 however i Think it has nothing to do with End-to-End layer 2 connectivity so it will be included in other topics which i Think you would have to look at from both a L2 and a L3 perspective such as .... Security & Multicast in perticular.
Technology: None specific, just Writing down some things to consider since Layer 2 studies and notes are now completed.
I did expect it to take a lot longer to go through the layer 2 sections of the Blueprint.
The time i wrote down during my studies of Layer 2 is not a direct representation of how much time i have invested in studying.
There is a lot of time to be added to Layer 2 studies that I've not taken the time to write down.
Here are some pieces that have required a lot of time that is not included in the time-required that i've written down:
-Writing down the study notes per technology.
-Browsing various forums, discussing various networking topics at other forums, Reading books, RFC's and other things.
-Doing research of how to prepare for the CCIE RSv5 including which videos to view, which topics to study, which vendor to work with, which platforms to use, which topology to use.
All-in-all....i wrote down my time required by working through the INE Topology and their CCIE RSv5 Workbook that I'm using.
That was my intention with these study notes so I know how much time i have invested with their Workbook in case i have to re-study something Before the Exam.
I can't estimate the time i've invested doing other things, but for those interested i will say it's an additional 100-150 hours except doing these labs and Reading the configuration guides!
Layer 2 topics saved for last:
....yes there is more to Layer 2 however i Think it has nothing to do with End-to-End layer 2 connectivity so it will be included in other topics which i Think you would have to look at from both a L2 and a L3 perspective such as .... Security & Multicast in perticular.
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum